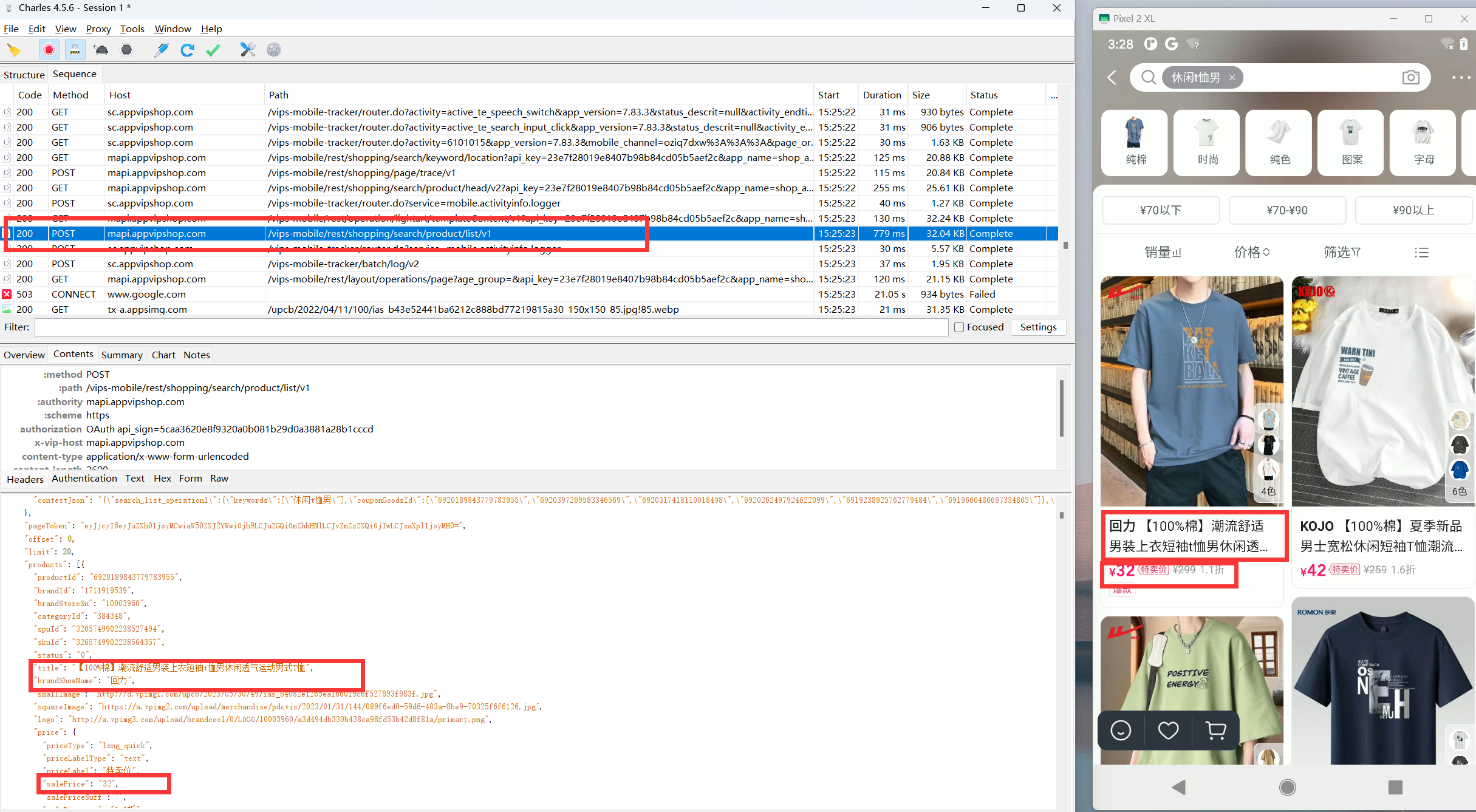
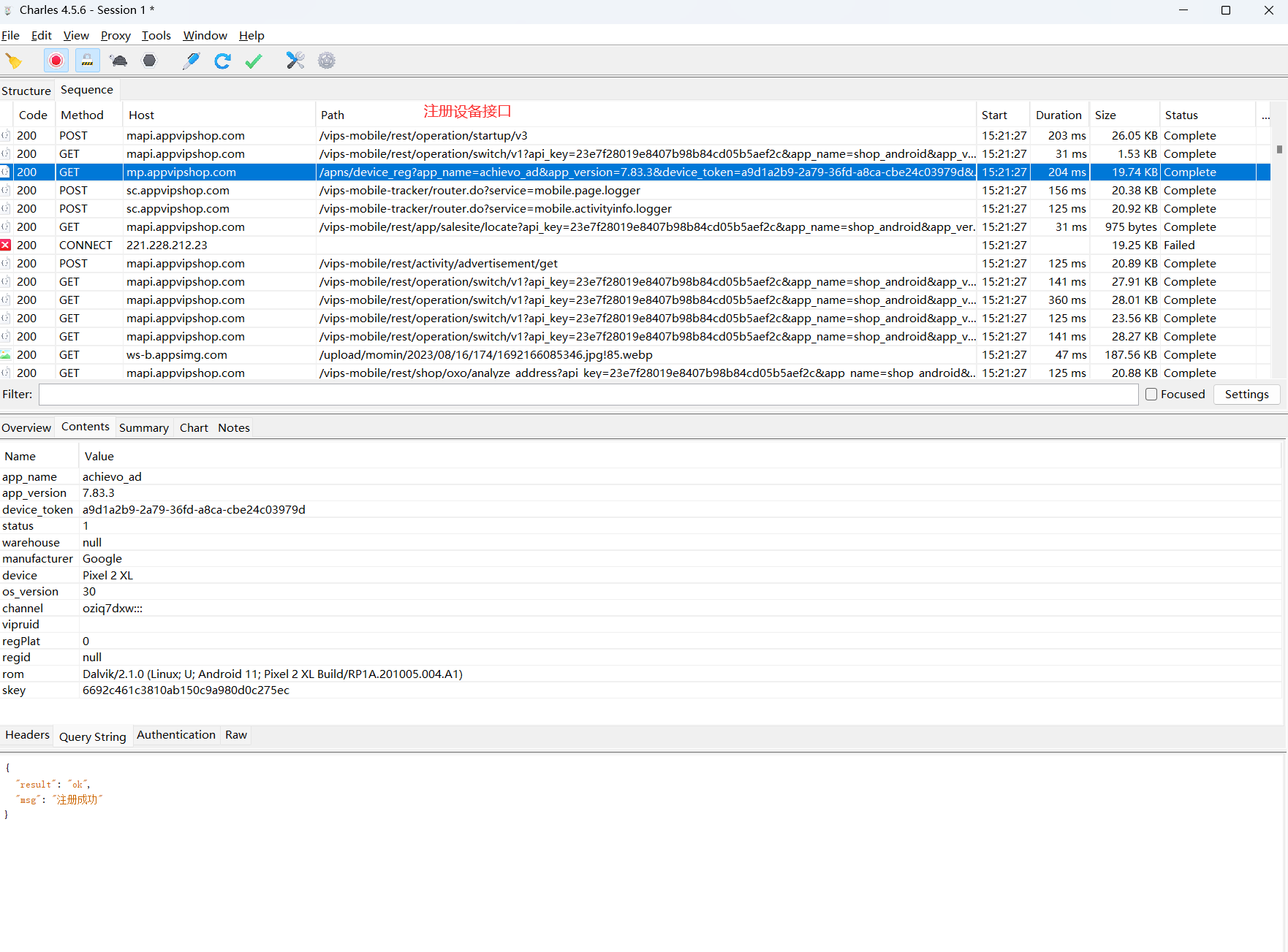
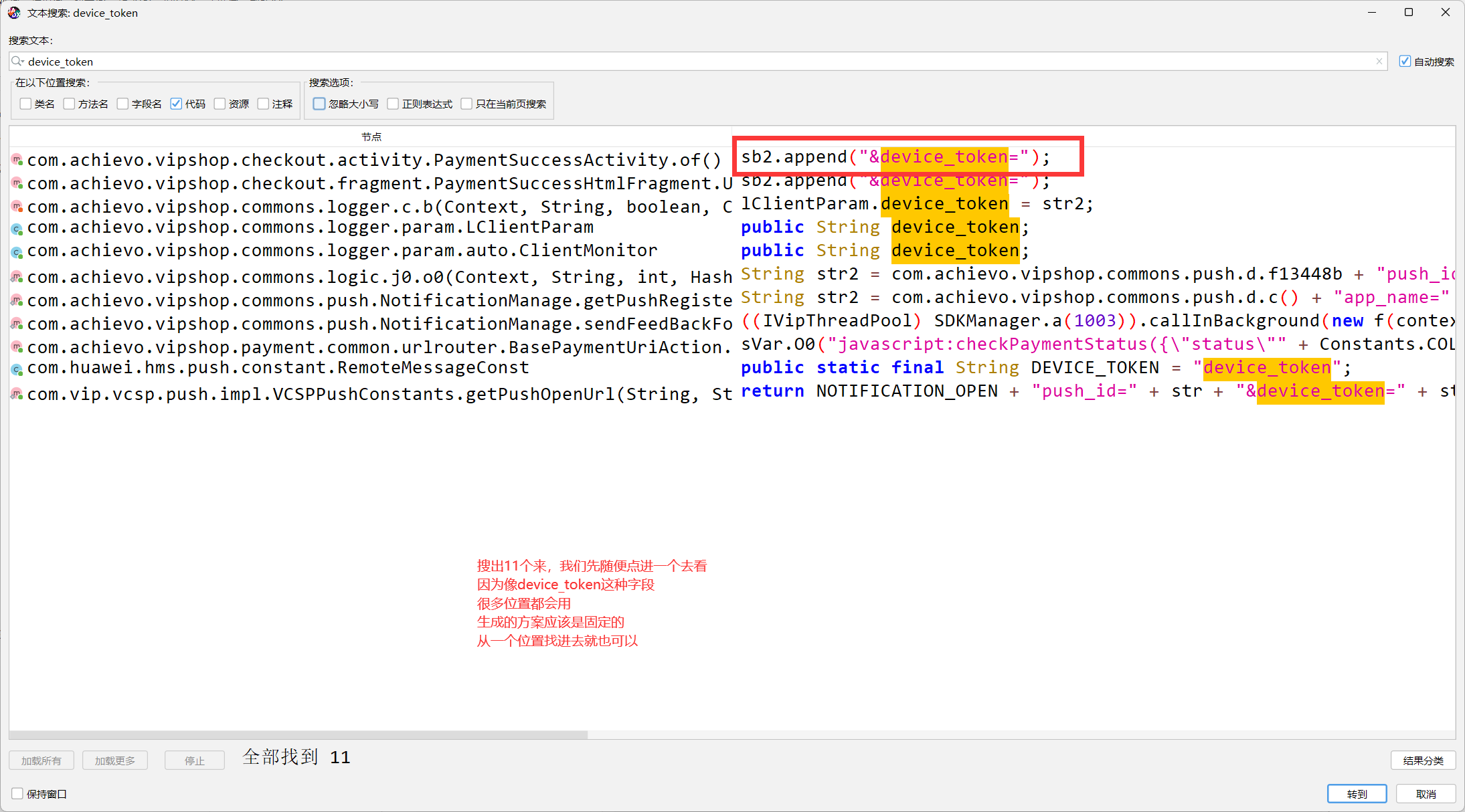
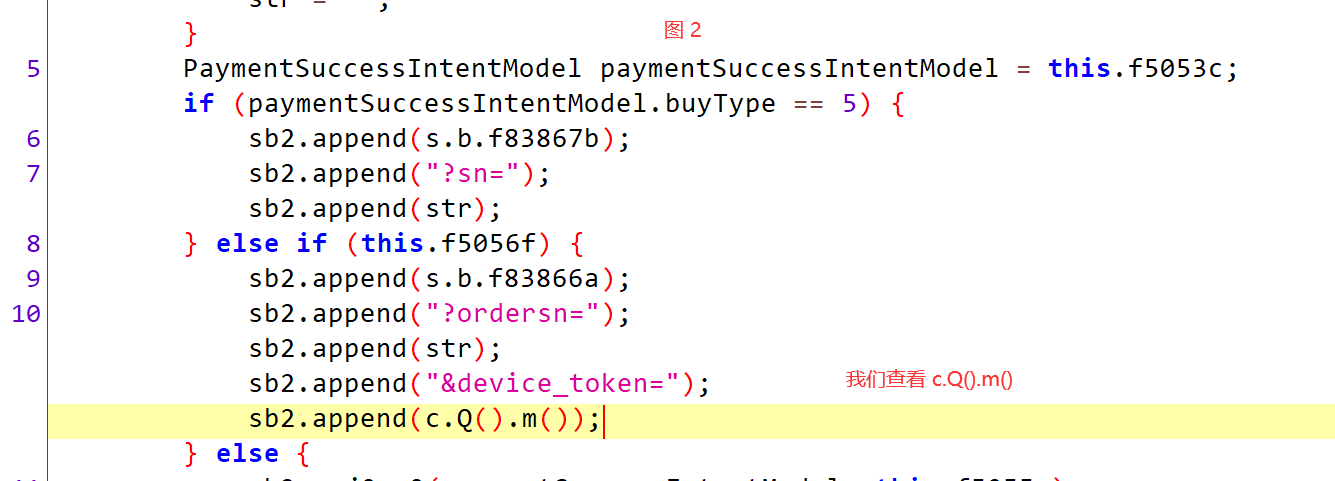
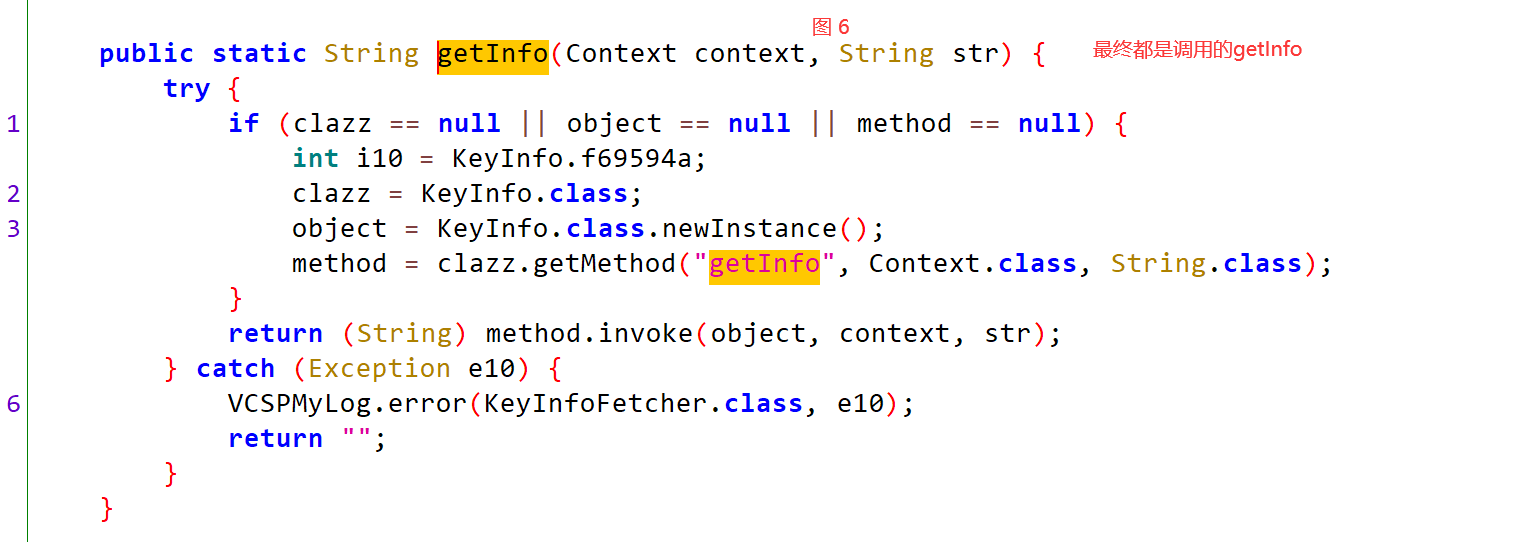
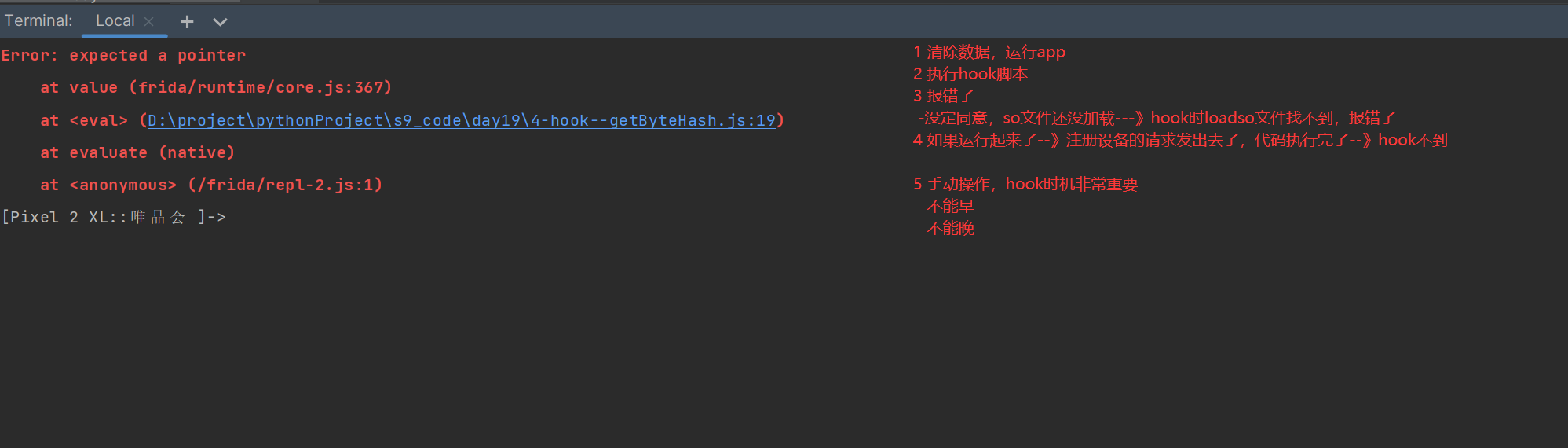
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
|
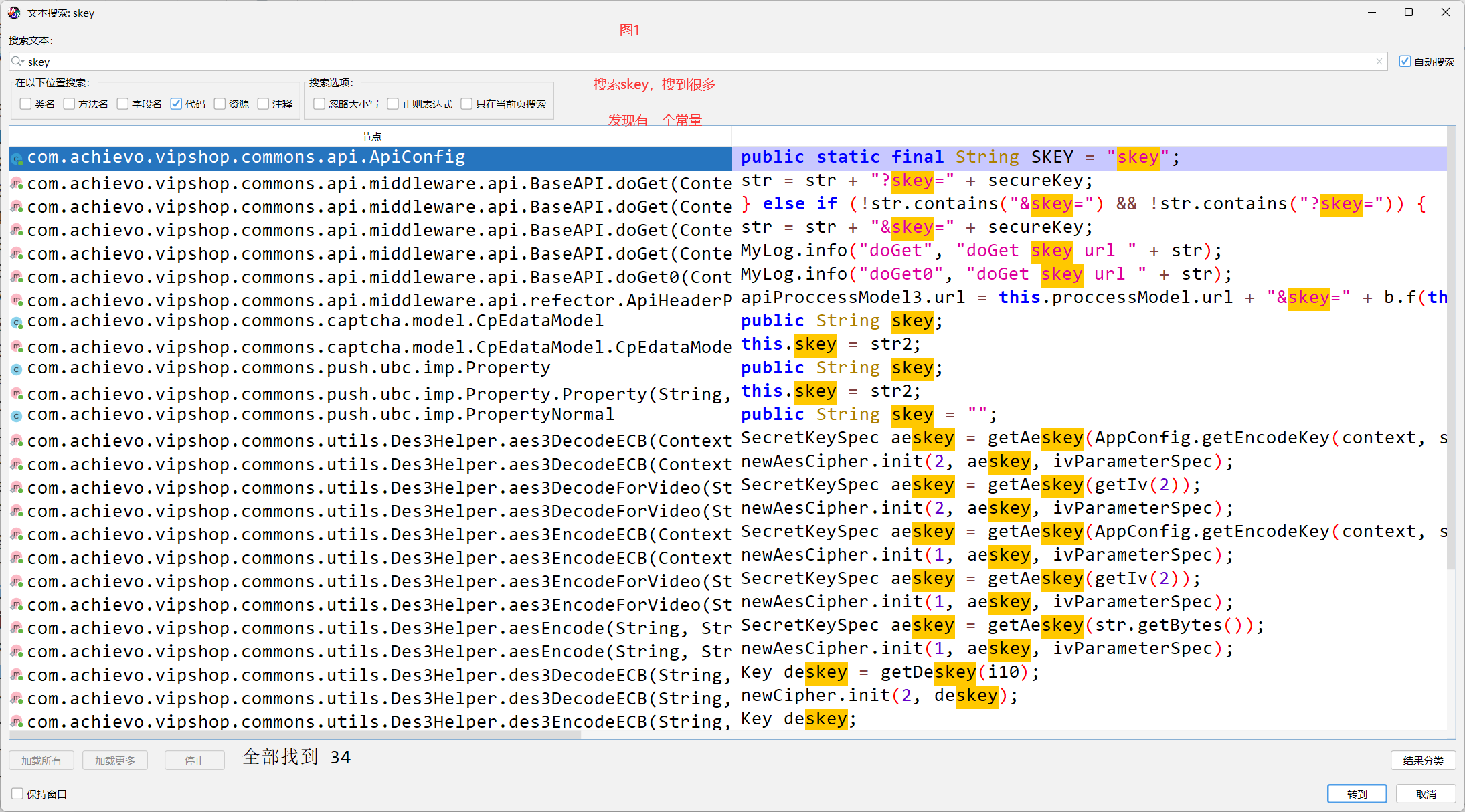
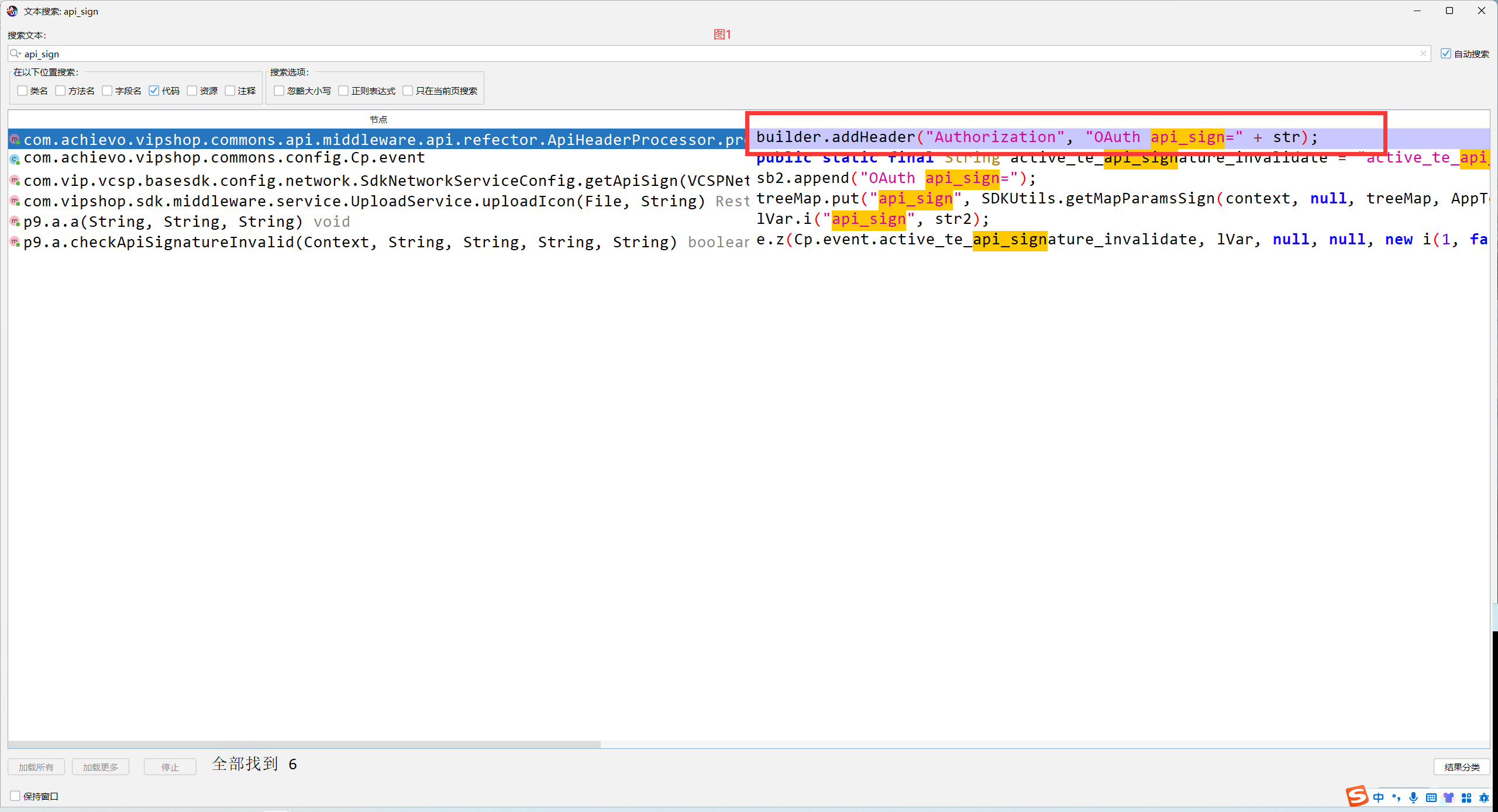
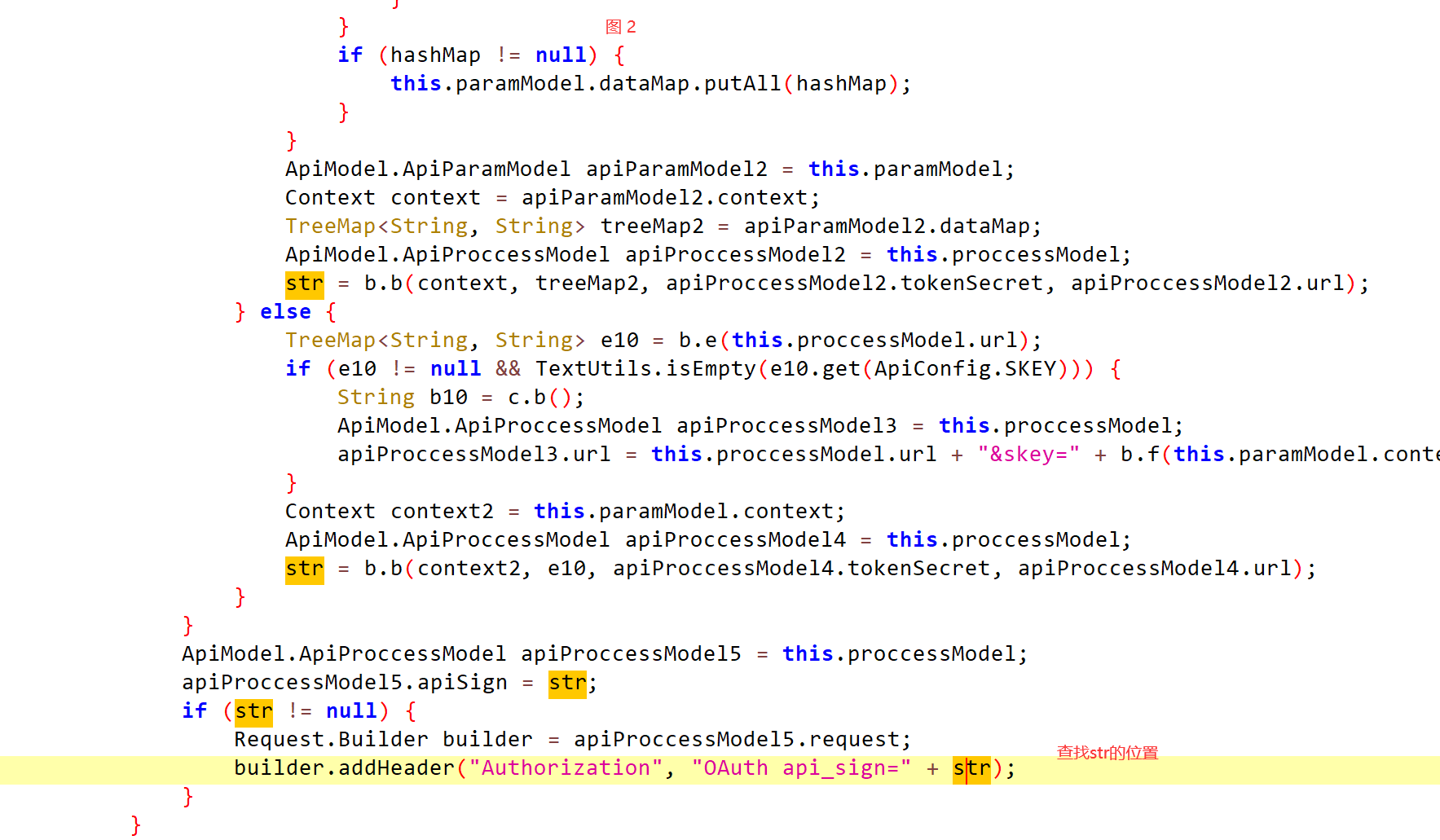
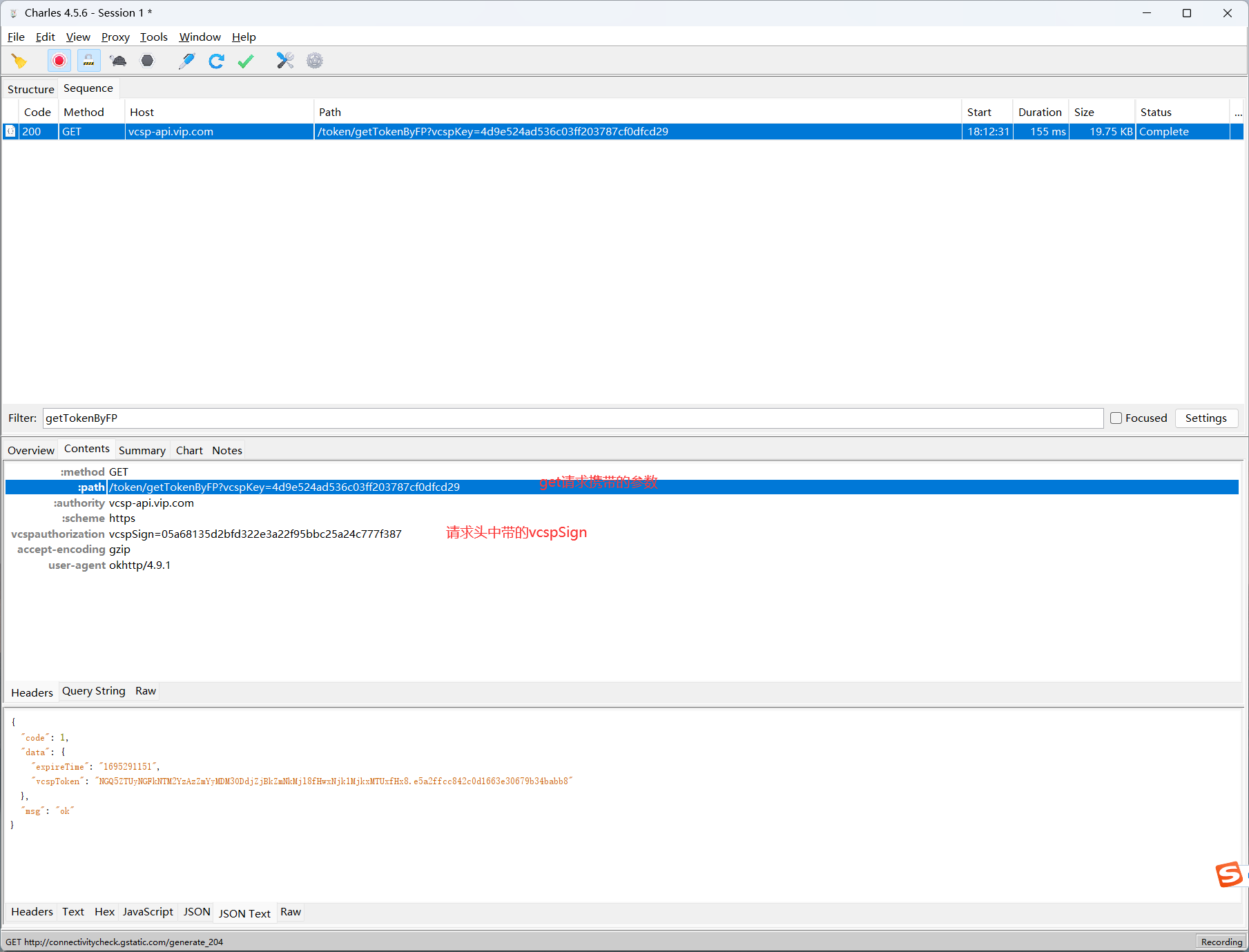
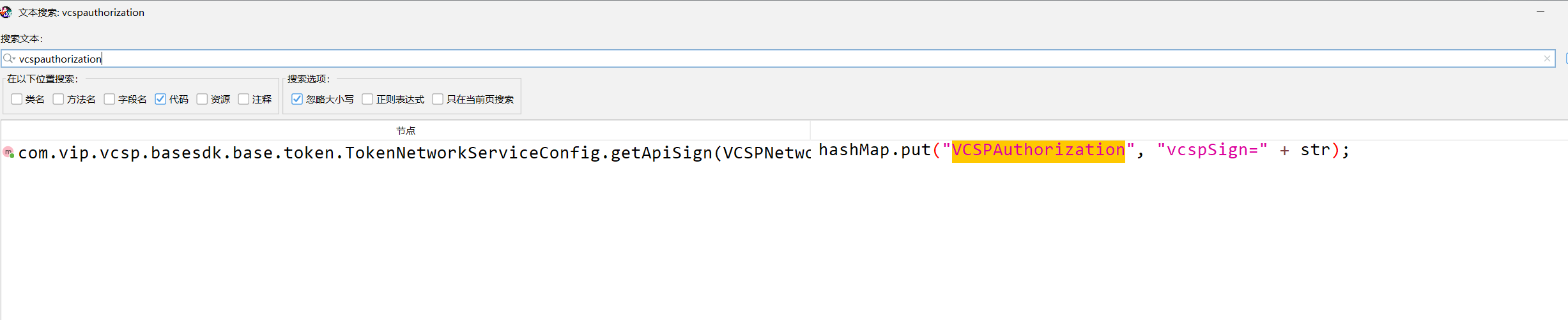
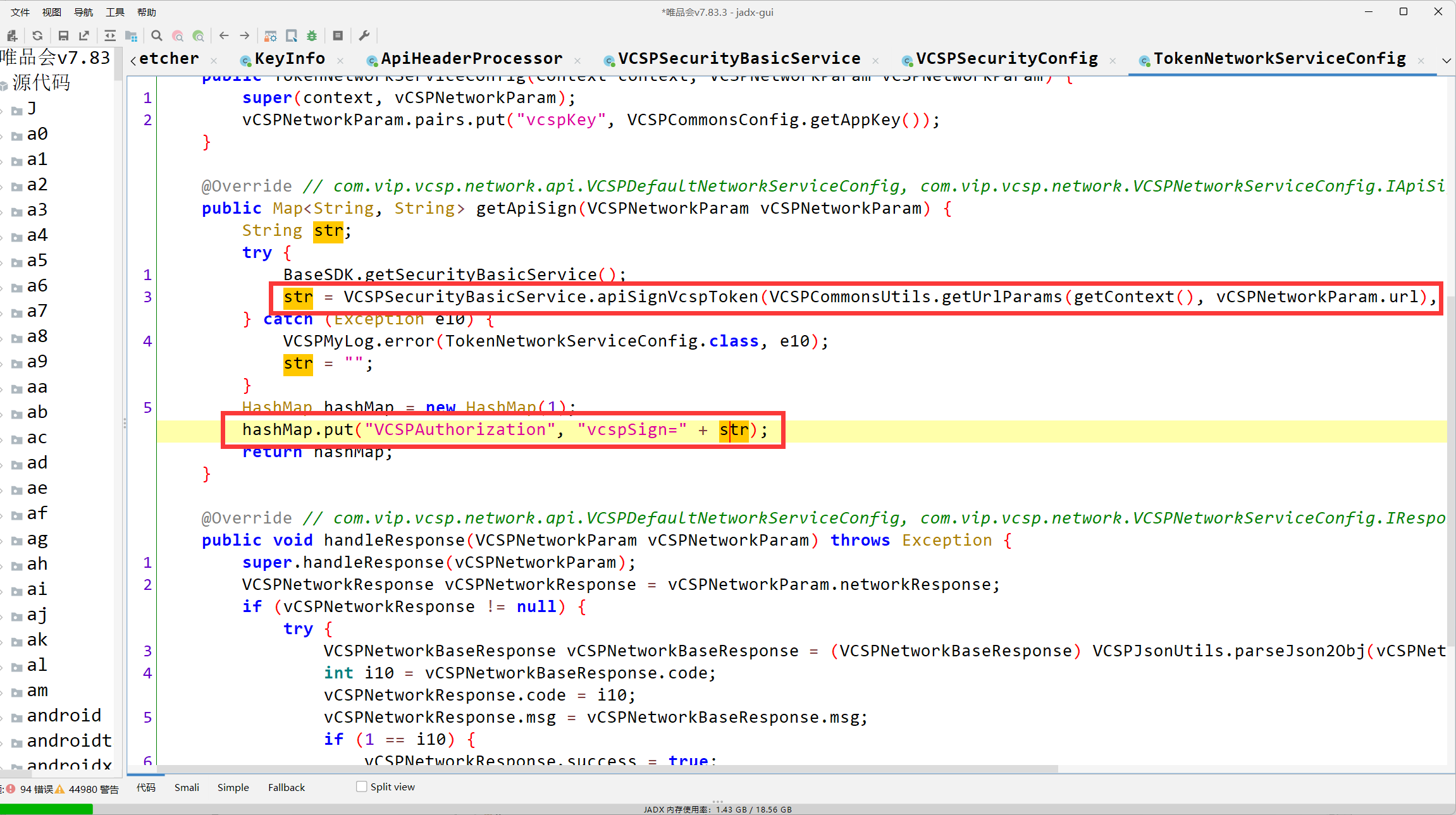
builder.addHeader("Authorization", "OAuth api_sign=" + str);
str = b.b()得到的
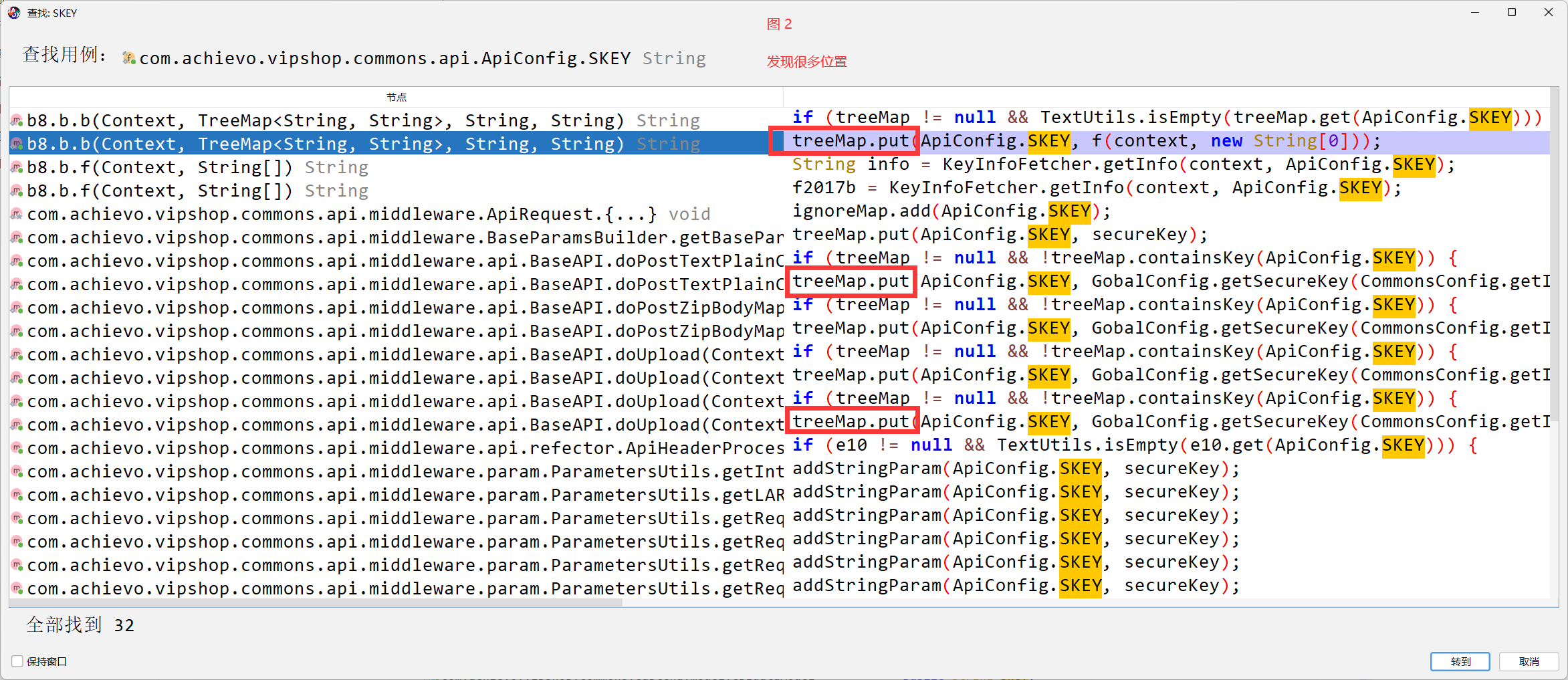
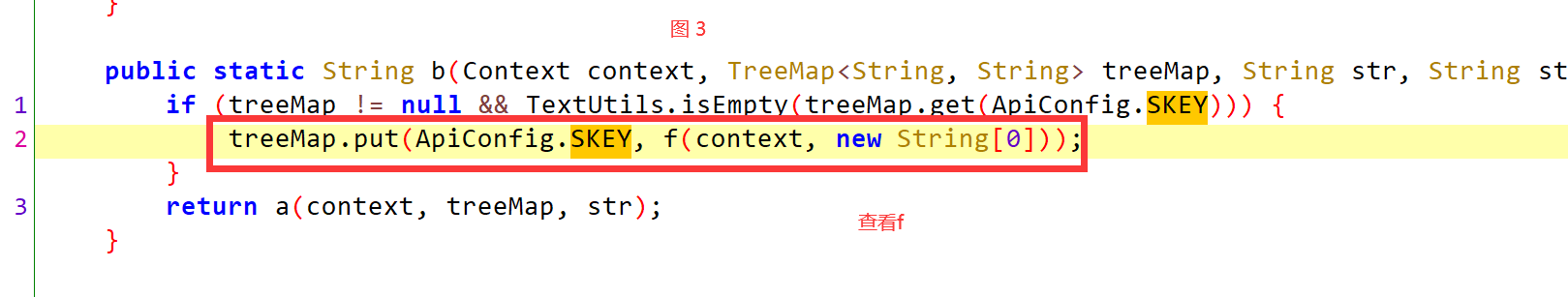
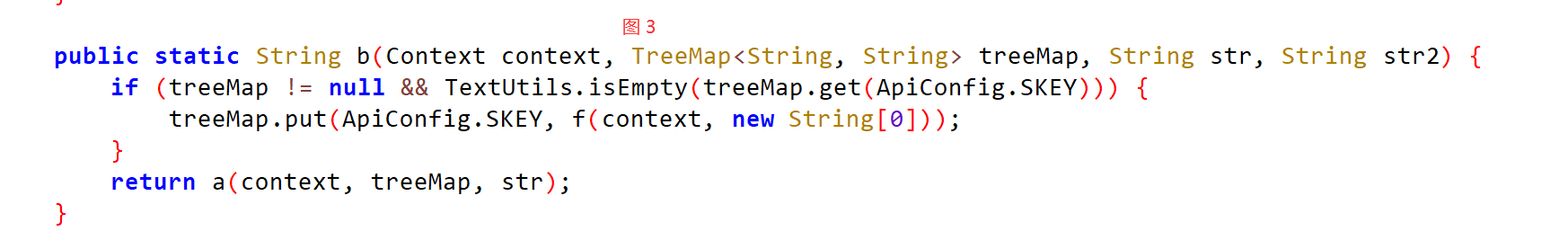
public static String b(Context context, TreeMap<String, String> treeMap, String str, String str2) {
if (treeMap != null && TextUtils.isEmpty(treeMap.get(ApiConfig.SKEY))) {
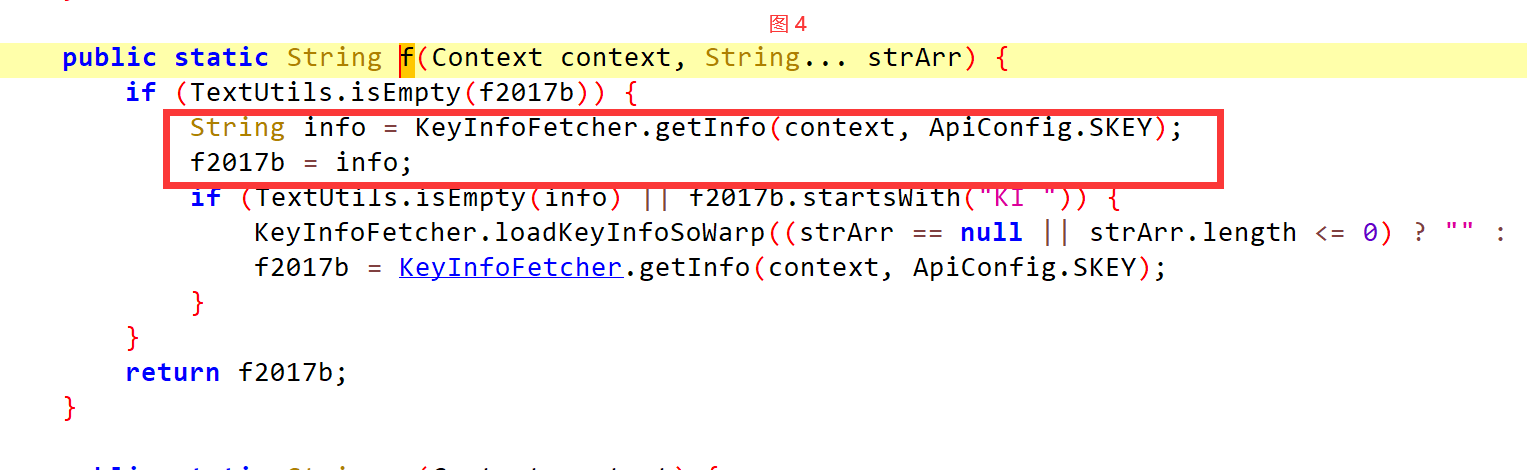
treeMap.put(ApiConfig.SKEY, f(context, new String[0]));
}
return a(context, treeMap, str);
}
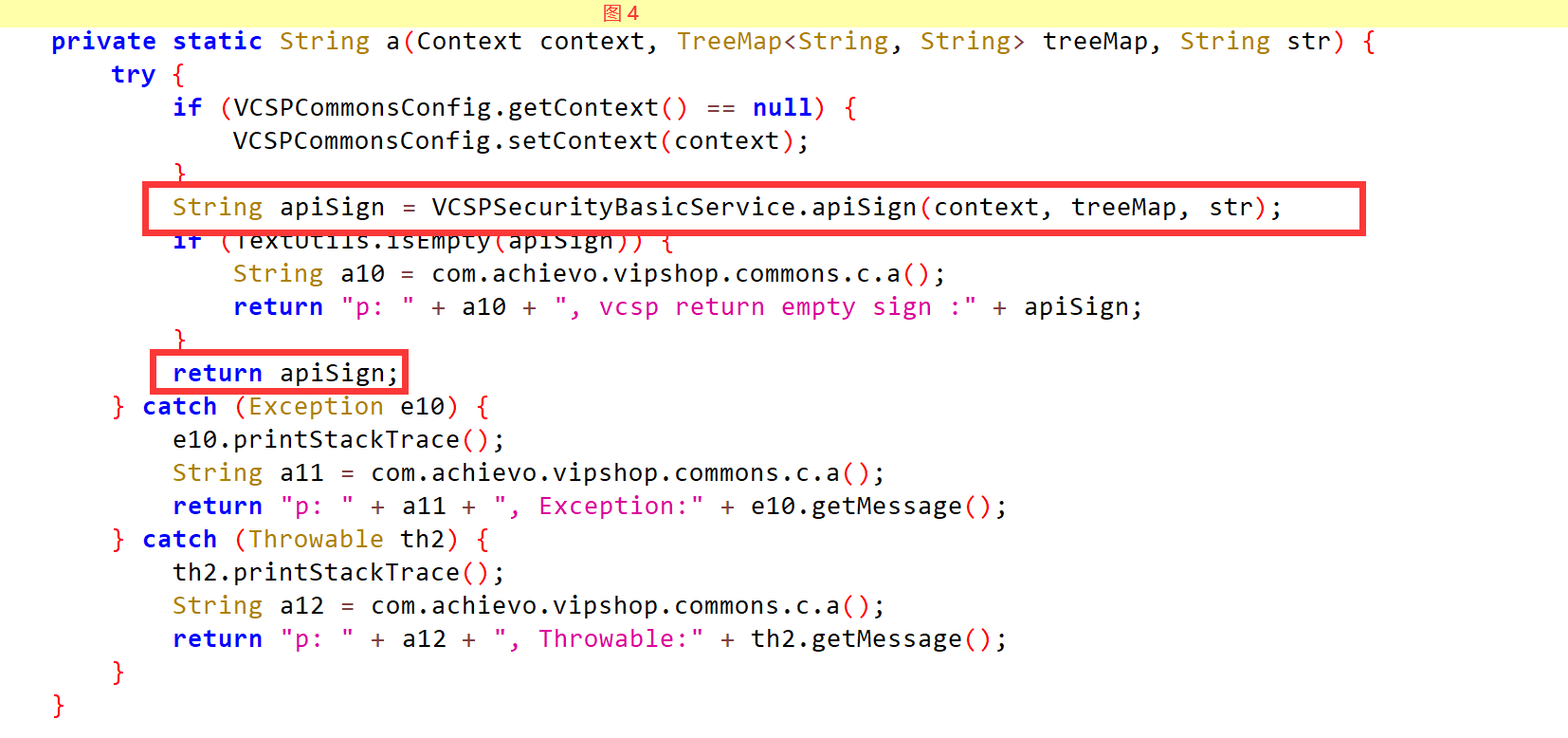
private static String a(Context context, TreeMap<String, String> treeMap, String str) {
try {
if (VCSPCommonsConfig.getContext() == null) {
VCSPCommonsConfig.setContext(context);
}
String apiSign = VCSPSecurityBasicService.apiSign(context, treeMap, str);
if (TextUtils.isEmpty(apiSign)) {
String a10 = com.achievo.vipshop.commons.c.a();
return "p: " + a10 + ", vcsp return empty sign :" + apiSign;
}
return apiSign;
} catch (Exception e10) {
e10.printStackTrace();
String a11 = com.achievo.vipshop.commons.c.a();
return "p: " + a11 + ", Exception:" + e10.getMessage();
} catch (Throwable th2) {
th2.printStackTrace();
String a12 = com.achievo.vipshop.commons.c.a();
return "p: " + a12 + ", Throwable:" + th2.getMessage();
}
}
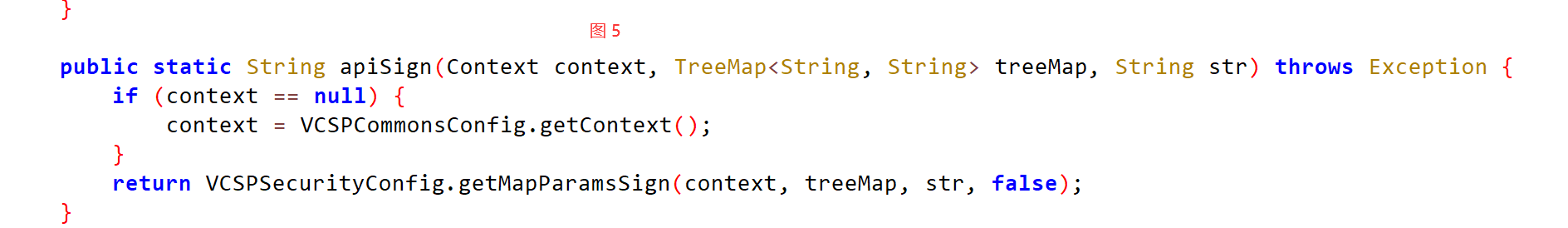
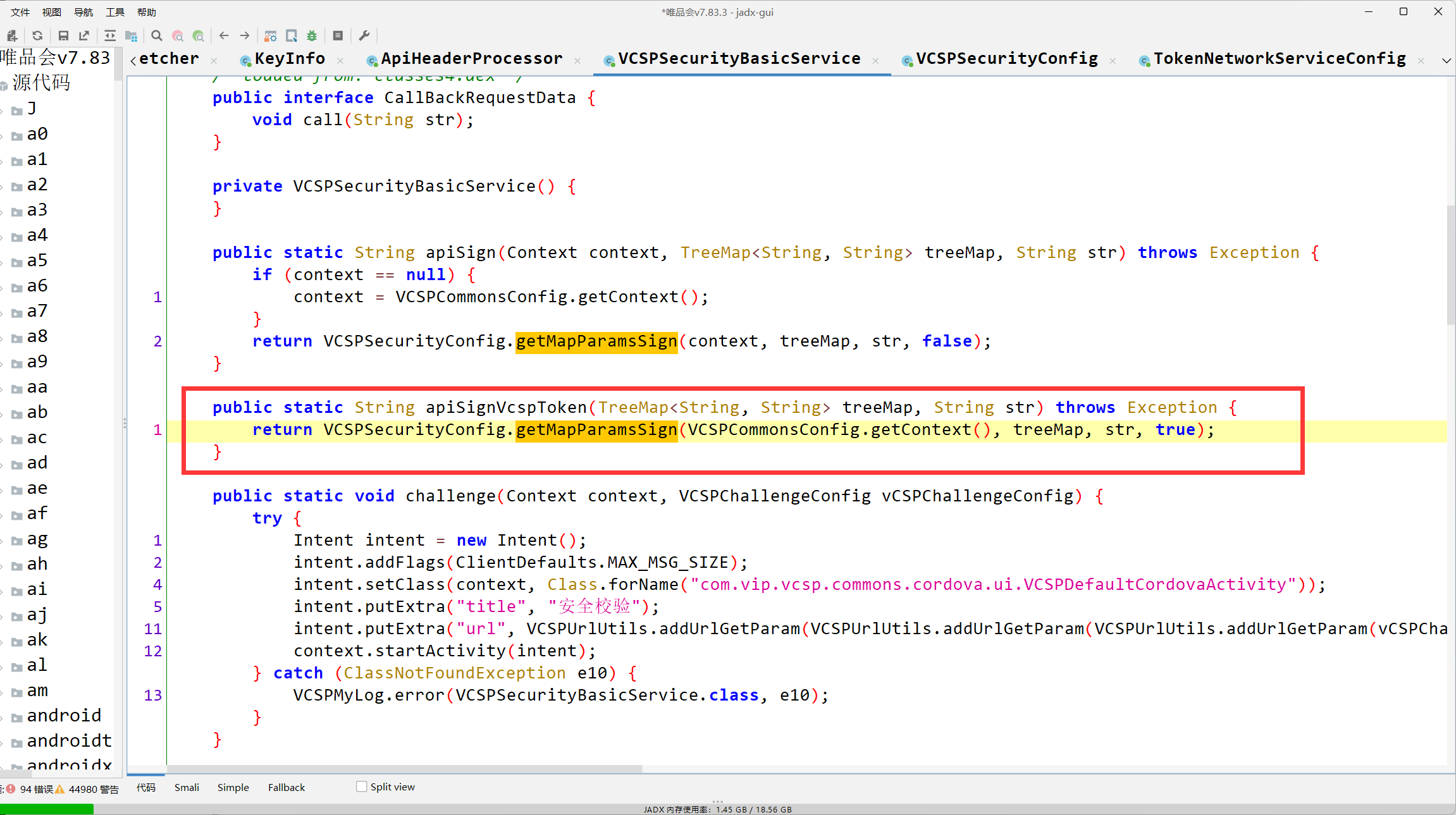
public static String apiSign(Context context, TreeMap<String, String> treeMap, String str) throws Exception {
if (context == null) {
context = VCSPCommonsConfig.getContext();
}
return VCSPSecurityConfig.getMapParamsSign(context, treeMap, str, false);
}
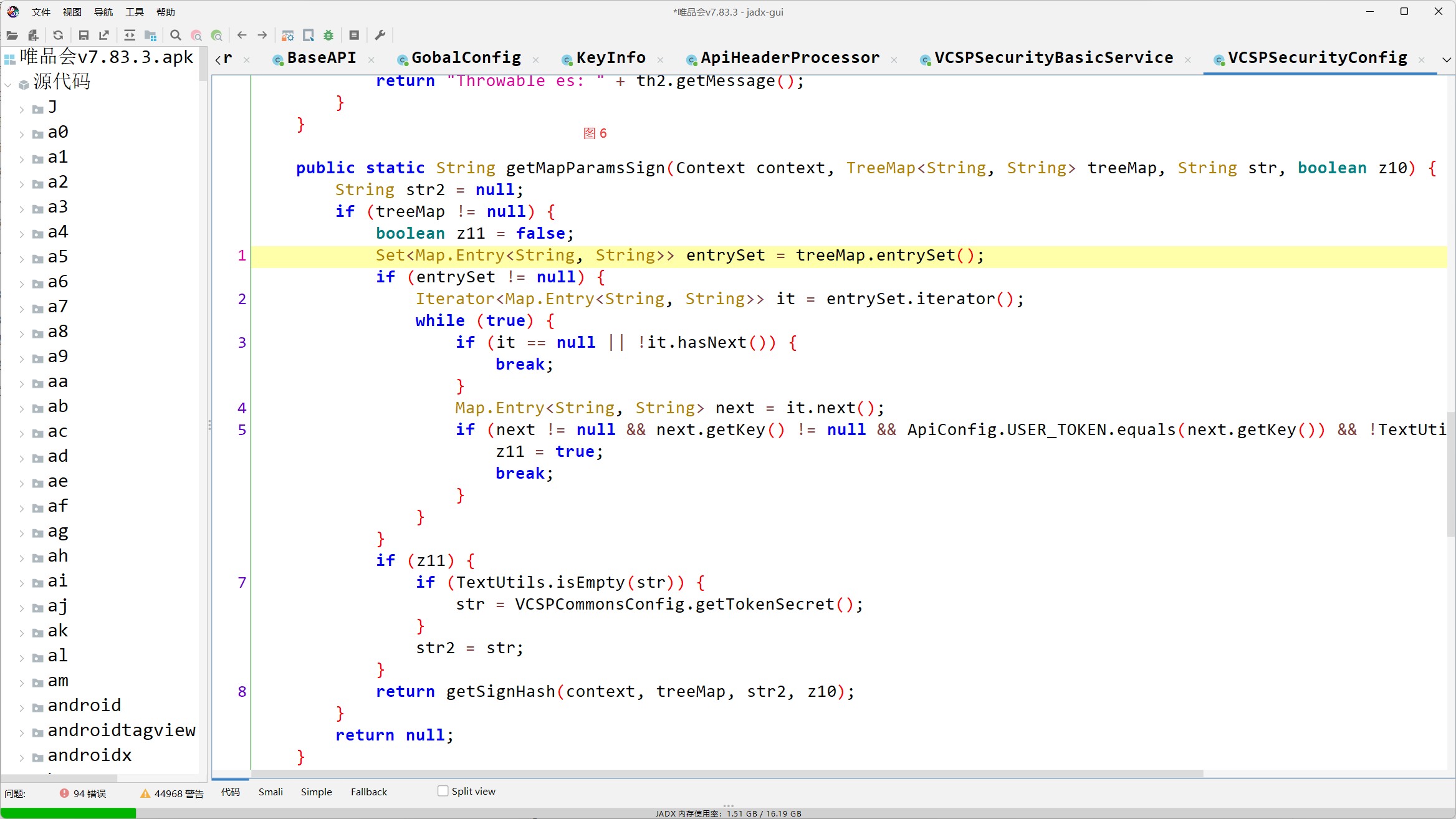
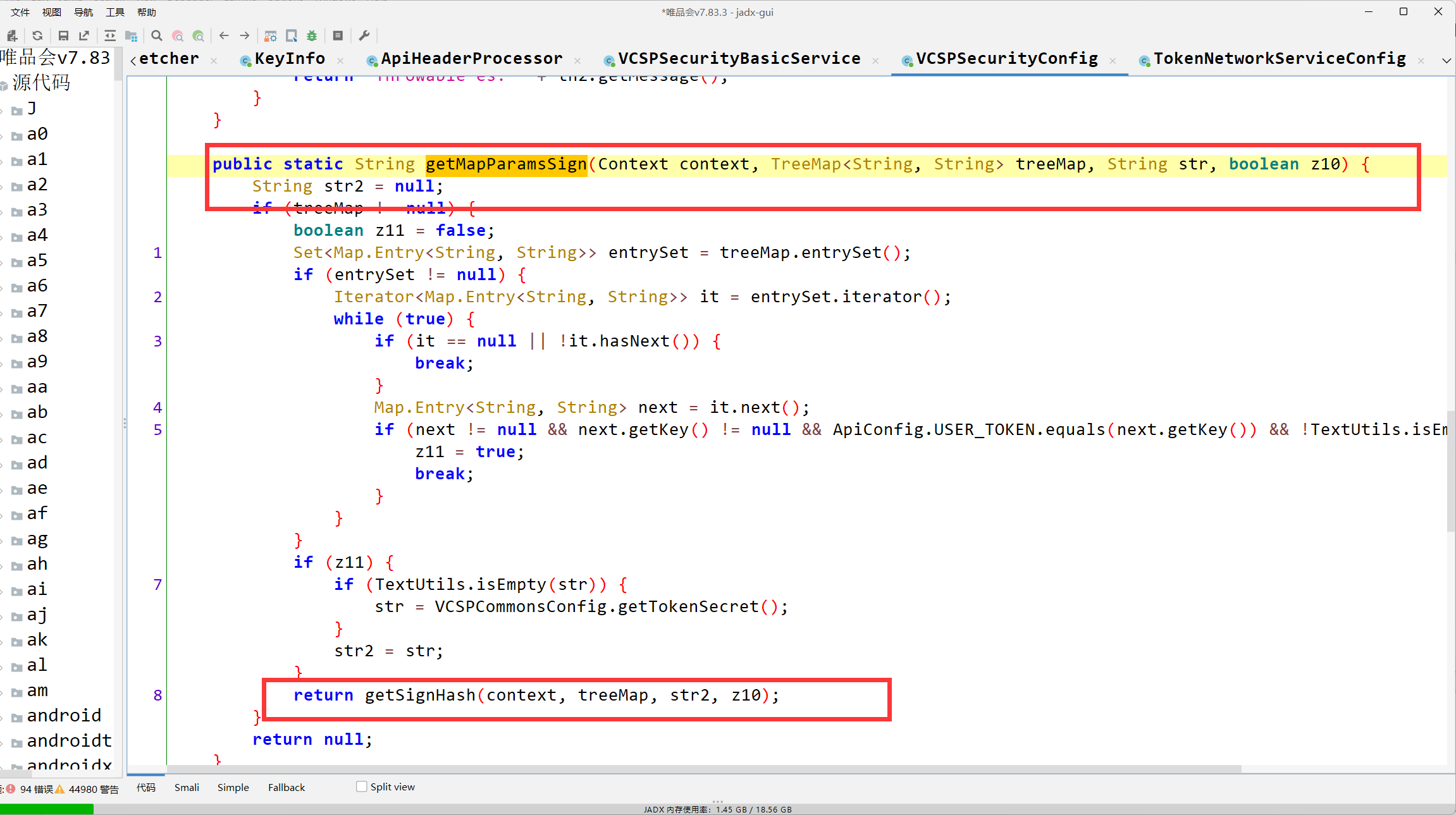
public static String getMapParamsSign(Context context, TreeMap<String, String> treeMap, String str, boolean z10) {
String str2 = null;
if (treeMap != null) {
boolean z11 = false;
Set<Map.Entry<String, String>> entrySet = treeMap.entrySet();
if (entrySet != null) {
Iterator<Map.Entry<String, String>> it = entrySet.iterator();
while (true) {
if (it == null || !it.hasNext()) {
break;
}
Map.Entry<String, String> next = it.next();
if (next != null && next.getKey() != null && ApiConfig.USER_TOKEN.equals(next.getKey()) && !TextUtils.isEmpty(next.getValue())) {
z11 = true;
break;
}
}
}
if (z11) {
if (TextUtils.isEmpty(str)) {
str = VCSPCommonsConfig.getTokenSecret();
}
str2 = str;
}
return getSignHash(context, treeMap, str2, z10);
}
return null;
}
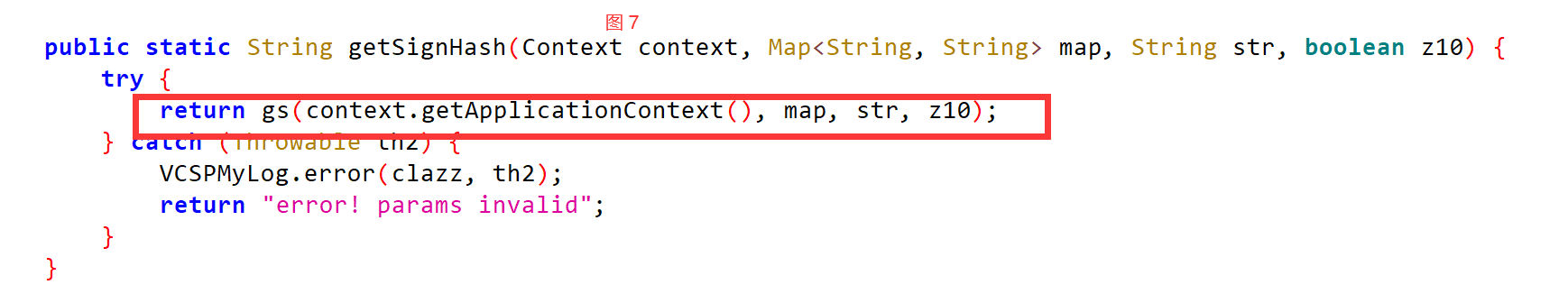
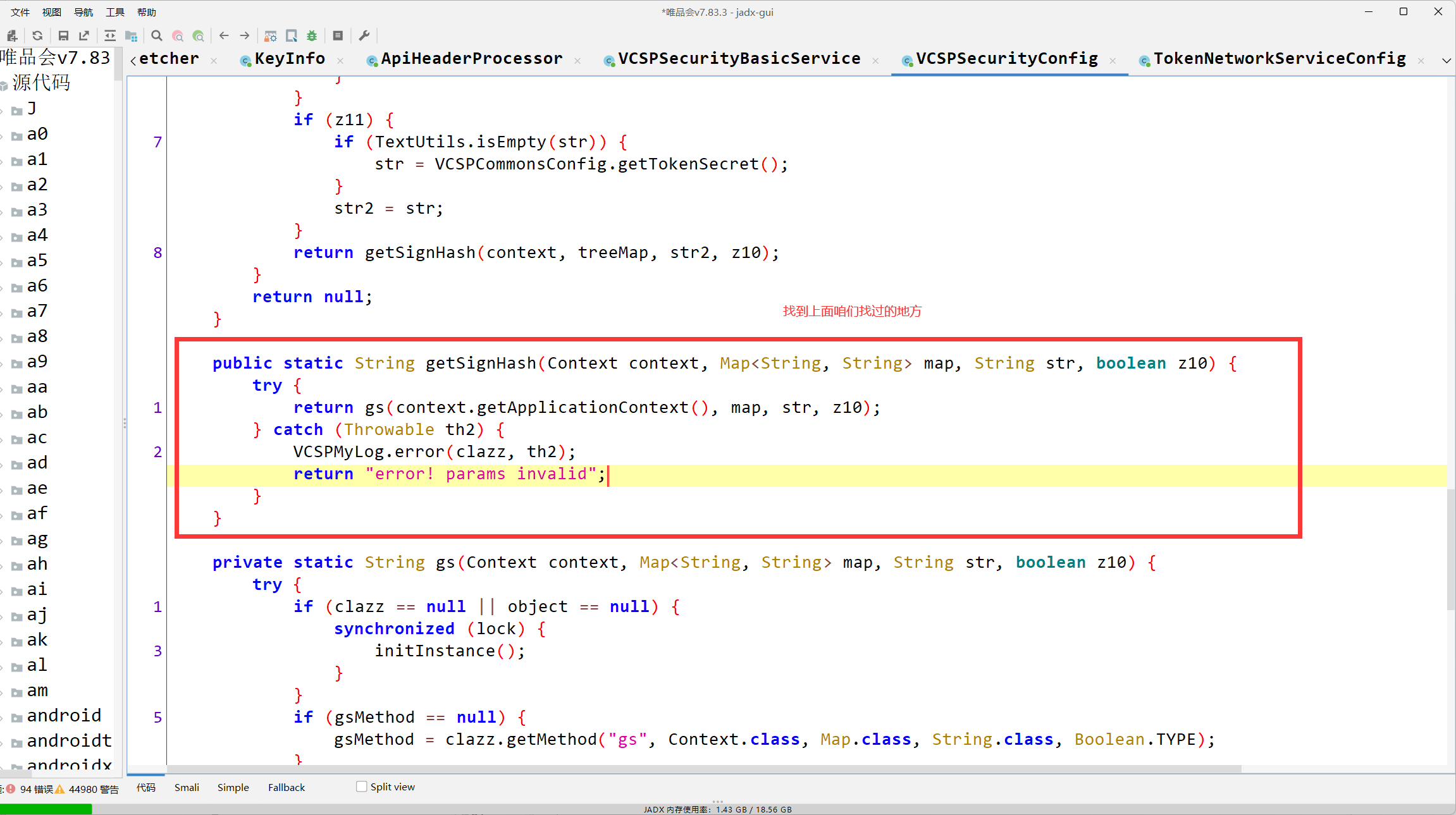
public static String getSignHash(Context context, Map<String, String> map, String str, boolean z10) {
try {
return gs(context.getApplicationContext(), map, str, z10);
} catch (Throwable th2) {
VCSPMyLog.error(clazz, th2);
return "error! params invalid";
}
}
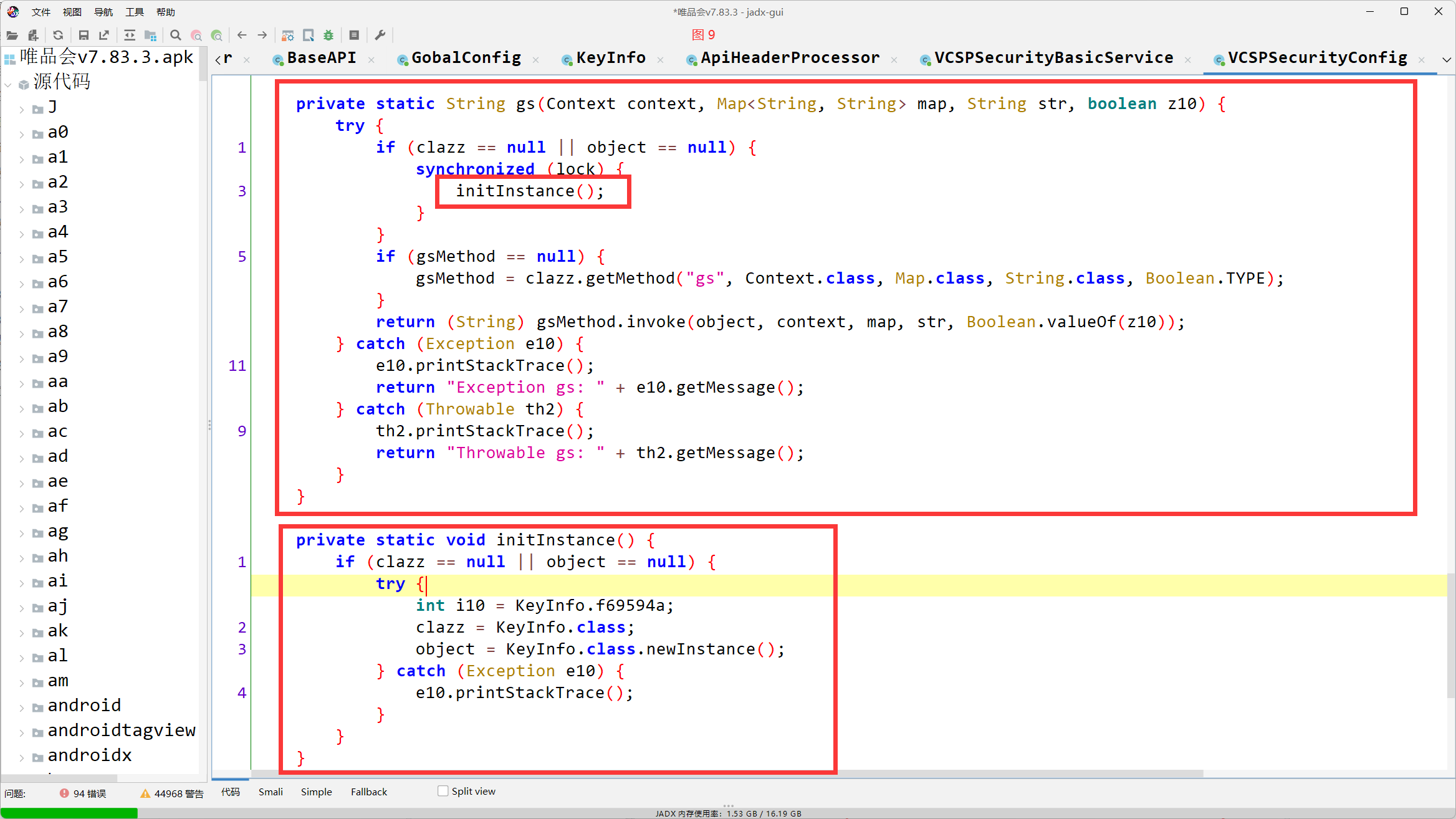
private static String gs(Context context, Map<String, String> map, String str, boolean z10) {
try {
if (clazz == null || object == null) {
synchronized (lock) {
initInstance();
}
}
if (gsMethod == null) {
gsMethod = clazz.getMethod("gs", Context.class, Map.class, String.class, Boolean.TYPE);
}
return (String) gsMethod.invoke(object, context, map, str, Boolean.valueOf(z10));
} catch (Exception e10) {
e10.printStackTrace();
return "Exception gs: " + e10.getMessage();
} catch (Throwable th2) {
th2.printStackTrace();
return "Throwable gs: " + th2.getMessage();
}
}
clazz = KeyInfo.class
object = KeyInfo.class.newInstance();
gsMethod = clazz.getMethod("gs", Context.class, Map.class, String.class, Boolean.TYPE);
gsMethod.invoke(object, context, map, str, Boolean.valueOf(z10))
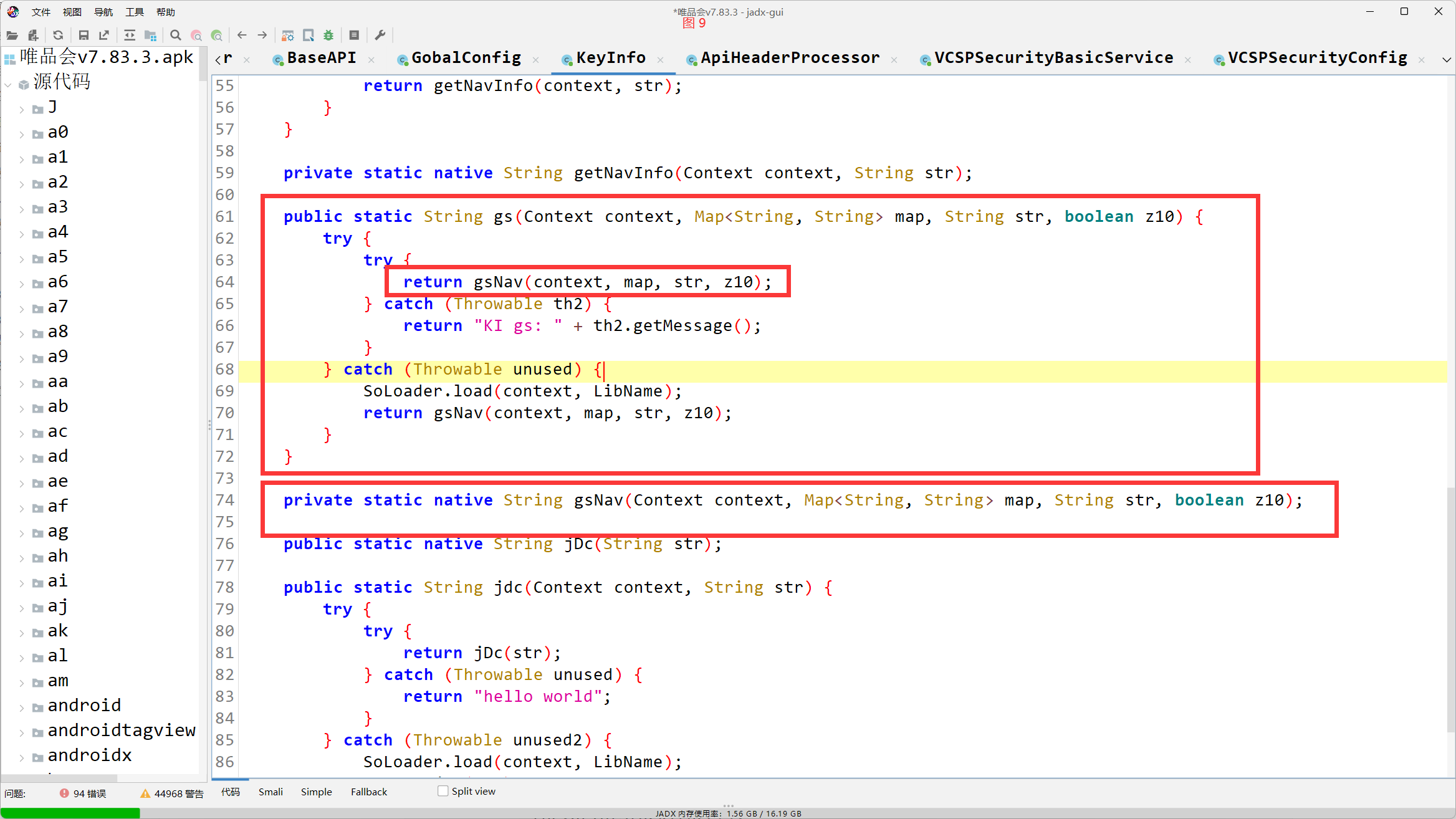
public static String gs(Context context, Map<String, String> map, String str, boolean z10) {
try {
try {
return gsNav(context, map, str, z10);
} catch (Throwable th2) {
return "KI gs: " + th2.getMessage();
}
} catch (Throwable unused) {
SoLoader.load(context, LibName);
return gsNav(context, map, str, z10);
}
}
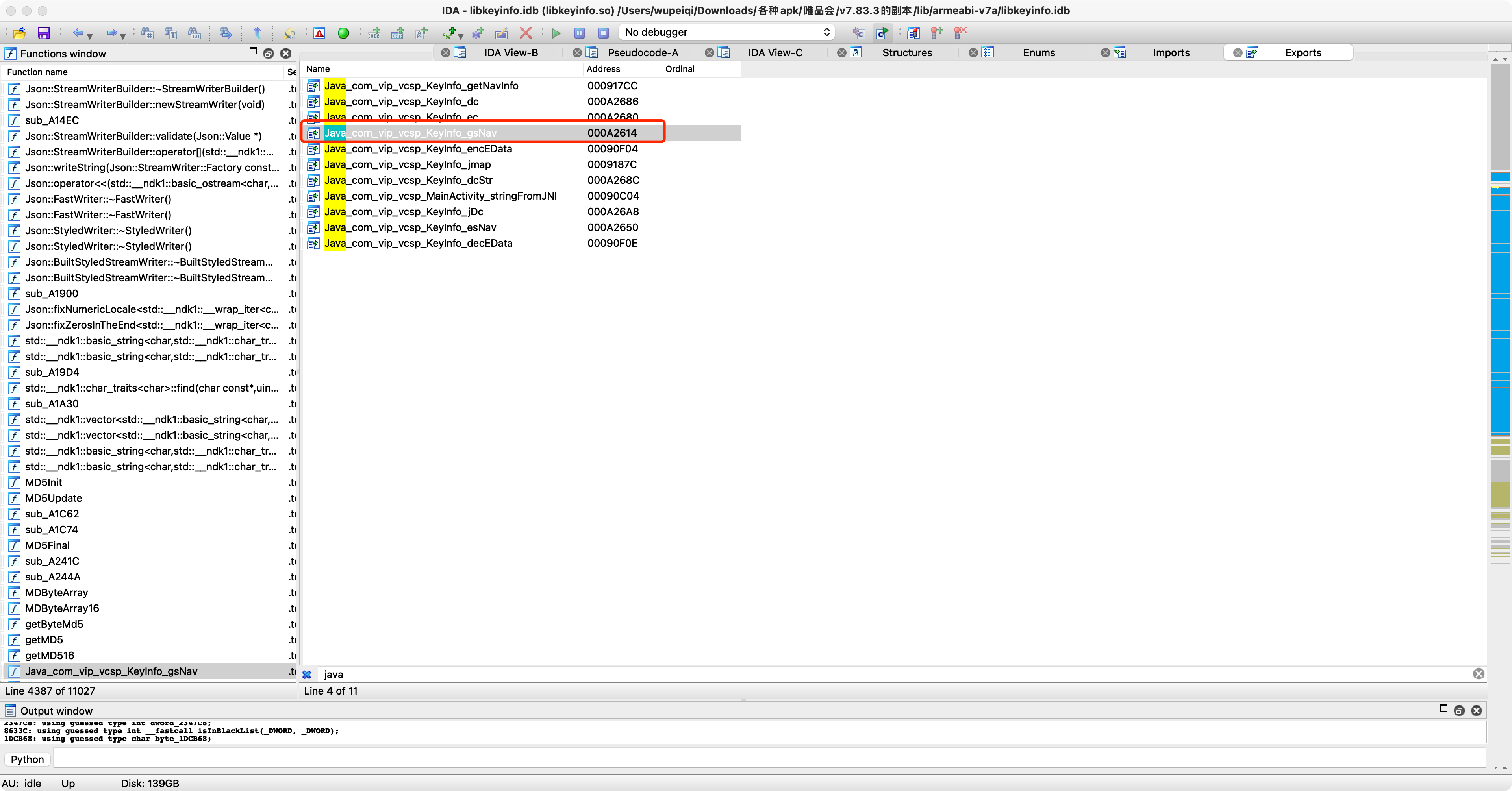
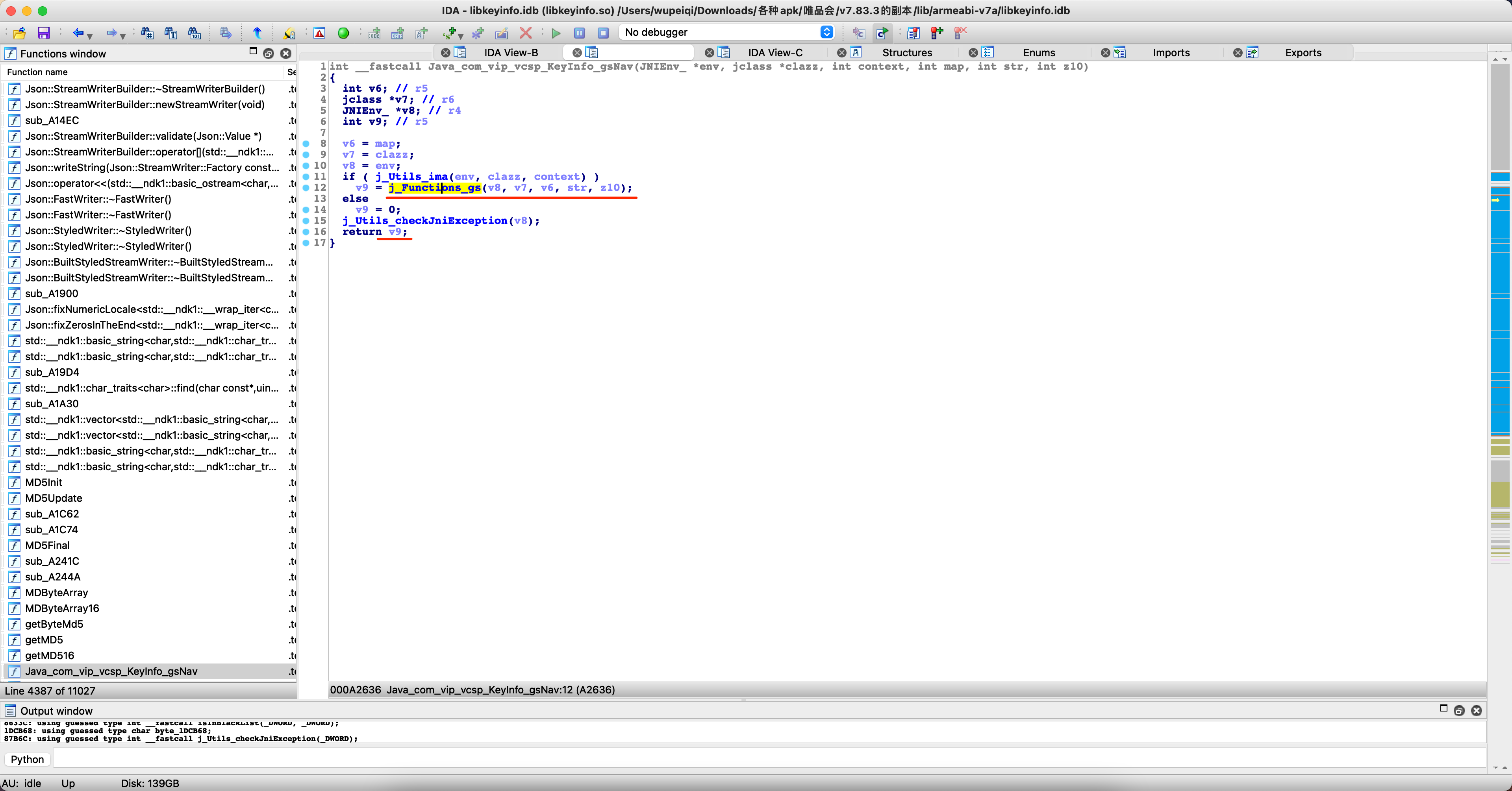
private static native String gsNav(Context context, Map<String, String> map, String str, boolean z10);
|