1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
|
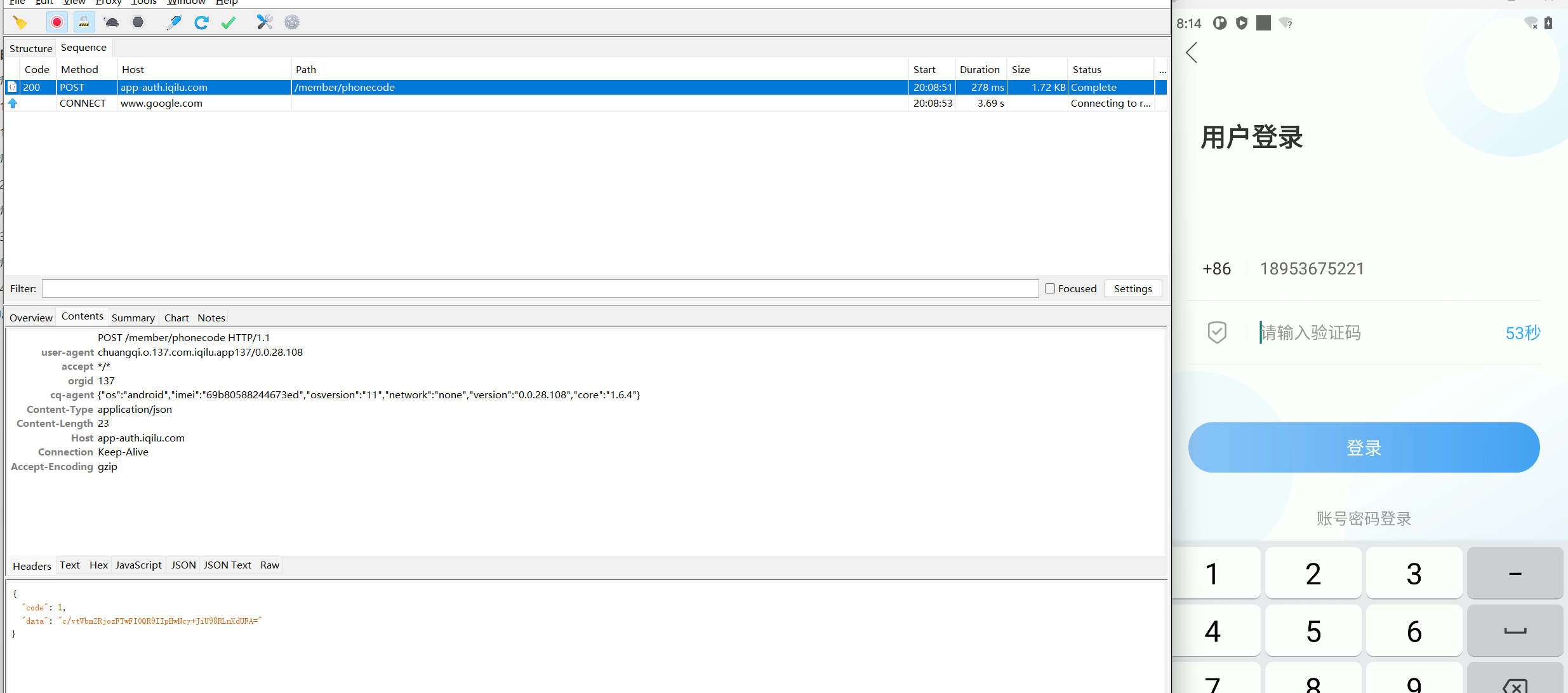
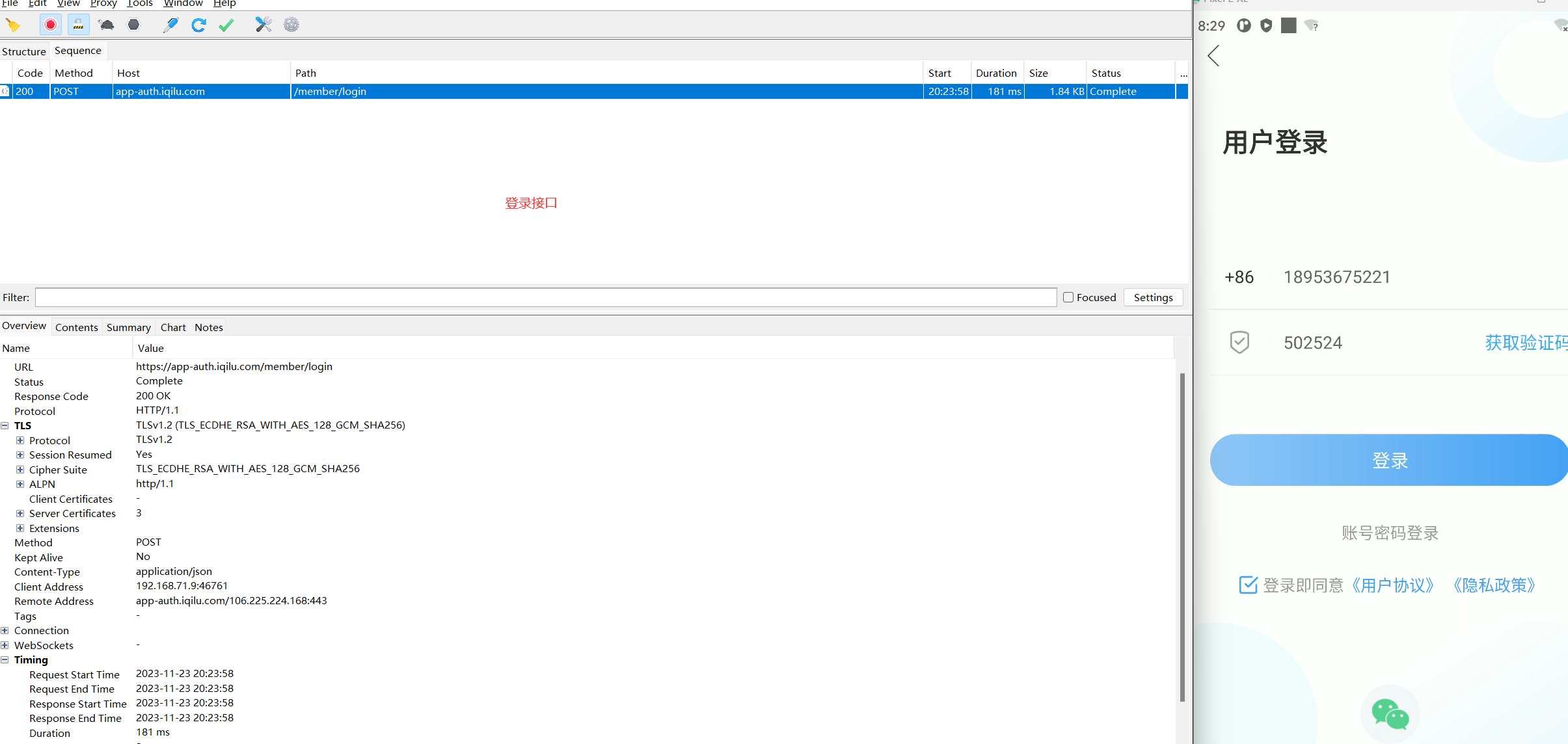
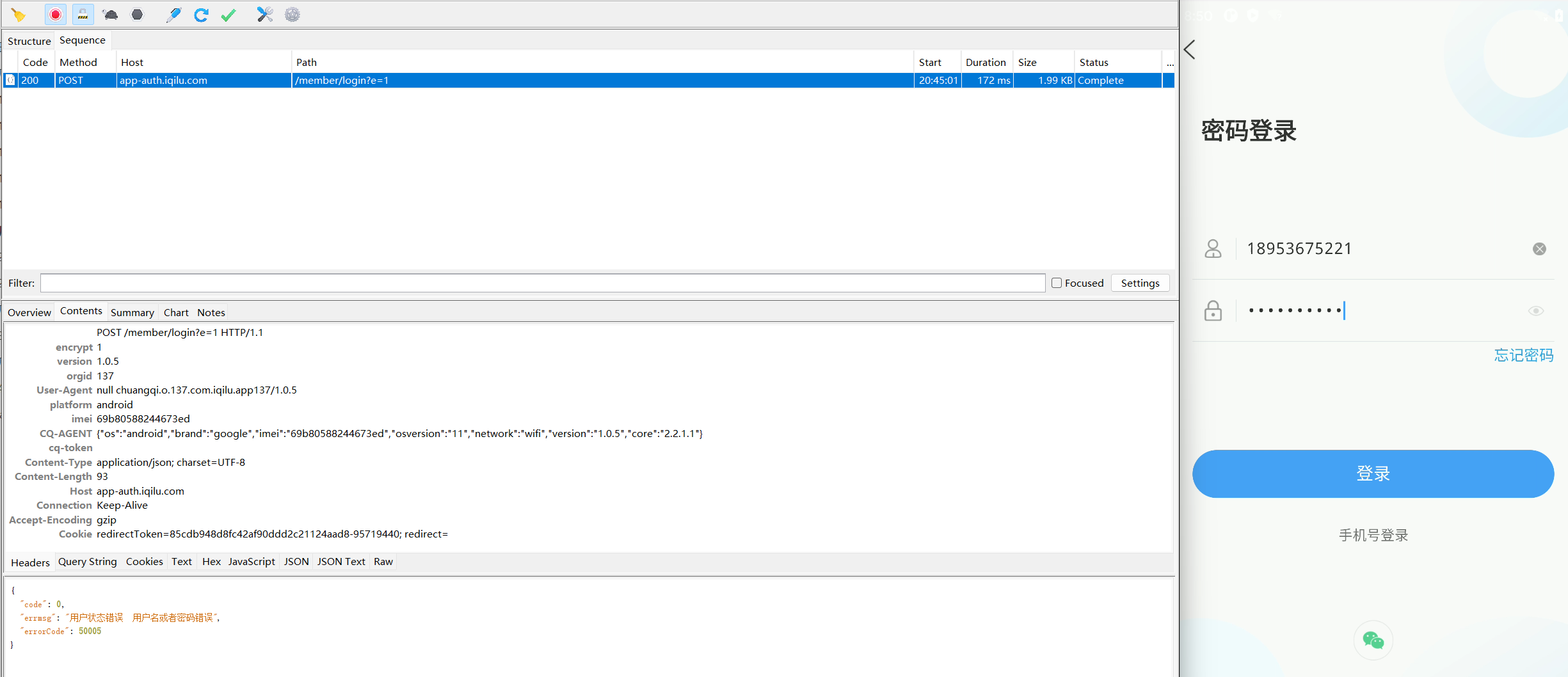
请求地址:
https://app-auth.iqilu.com/member/login?e=1
请求方式:
post
请求头:
encrypt 1
version 1.0.5
orgid 137
User-Agent null chuangqi.o.137.com.iqilu.app137/1.0.5
platform android
imei 69b80588244673ed
CQ-AGENT
cq-token
Content-Type
Content-Length
Host
Connection
Accept-Encoding gzip
Cookie
请求体:
{
"codeKey": "",
"password": "Y8rl9EvasBy6rozuyUytsw==",
"code": "",
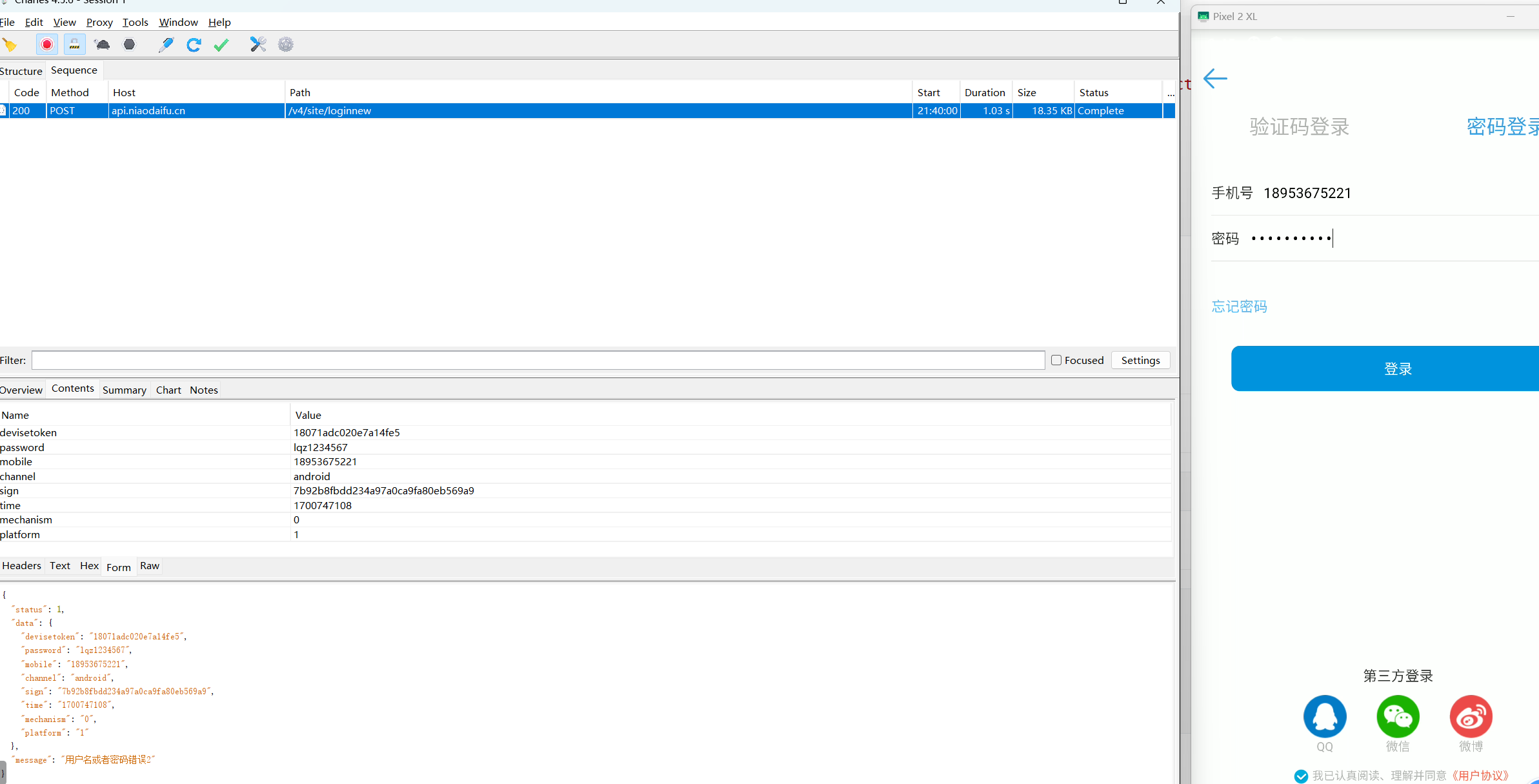
"phone": "18953675221",
"key": ""
}
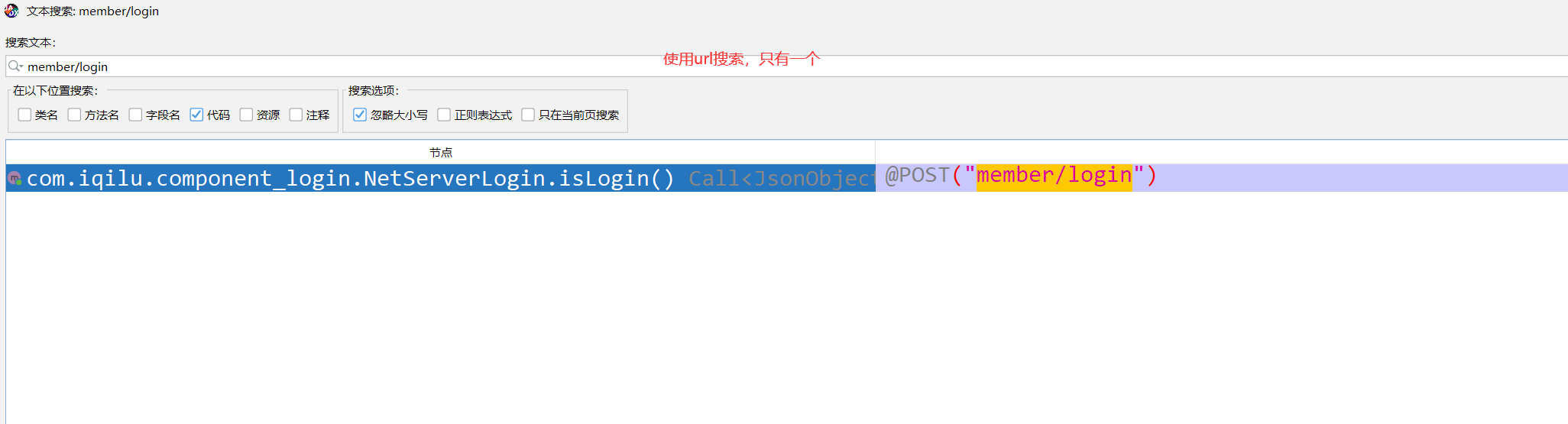
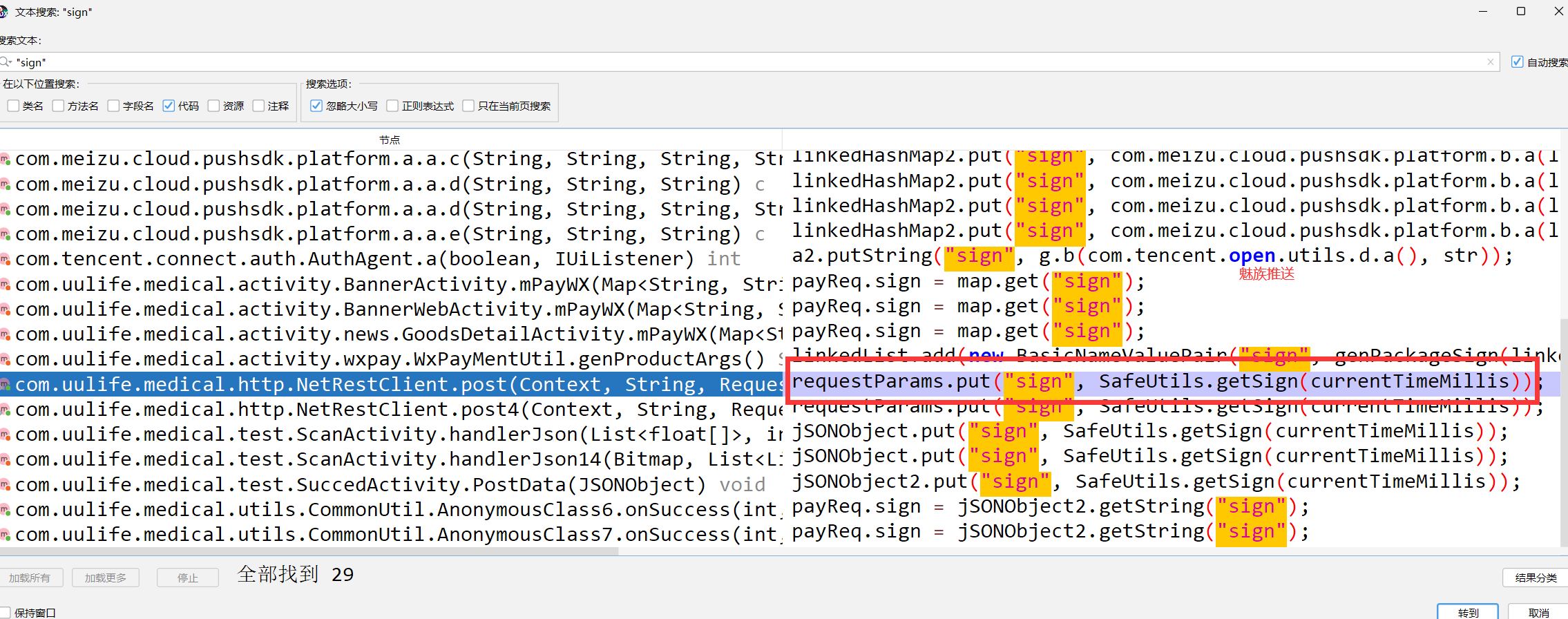
-根据关键字搜索:password "password" "password
-优先用url搜索:会唯一 member/login
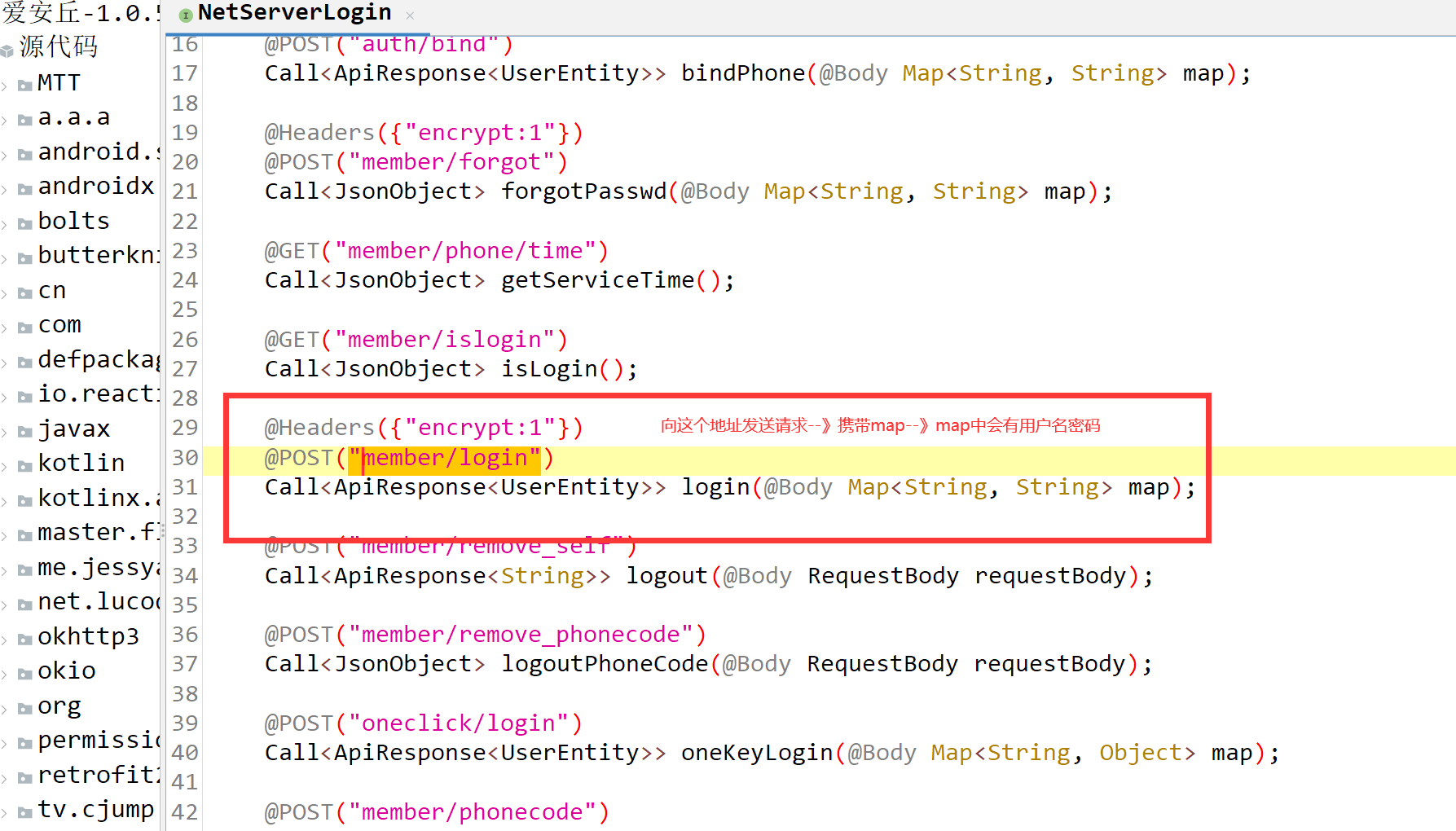
# 4 看到如下---》java代码你们看不懂---》现在只需要听
@Headers({"encrypt:1"})
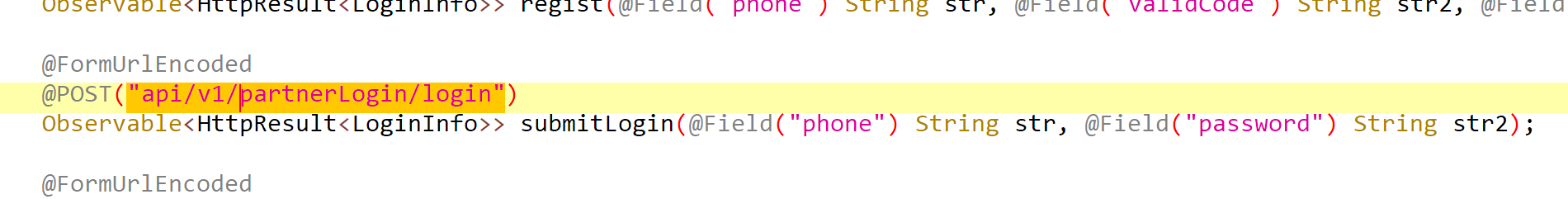
@POST("member/login")
Call<ApiResponse<UserEntity>> login(@Body Map<String, String> map);
# 5 查找用例 login 查找login谁用了,右键--》查找用例,发现一条---》双击过来
# 6 看到代码
public void login(Map<String, String> map, BaseCallBack<ApiResponse<UserEntity>> baseCallBack) {
requestData(ApiLogin.getInstance().login(map), baseCallBack);
}
# 7 找到谁调用了 login 函数,传入了map--》在上面的login 上点查找用例
# 8 找到了
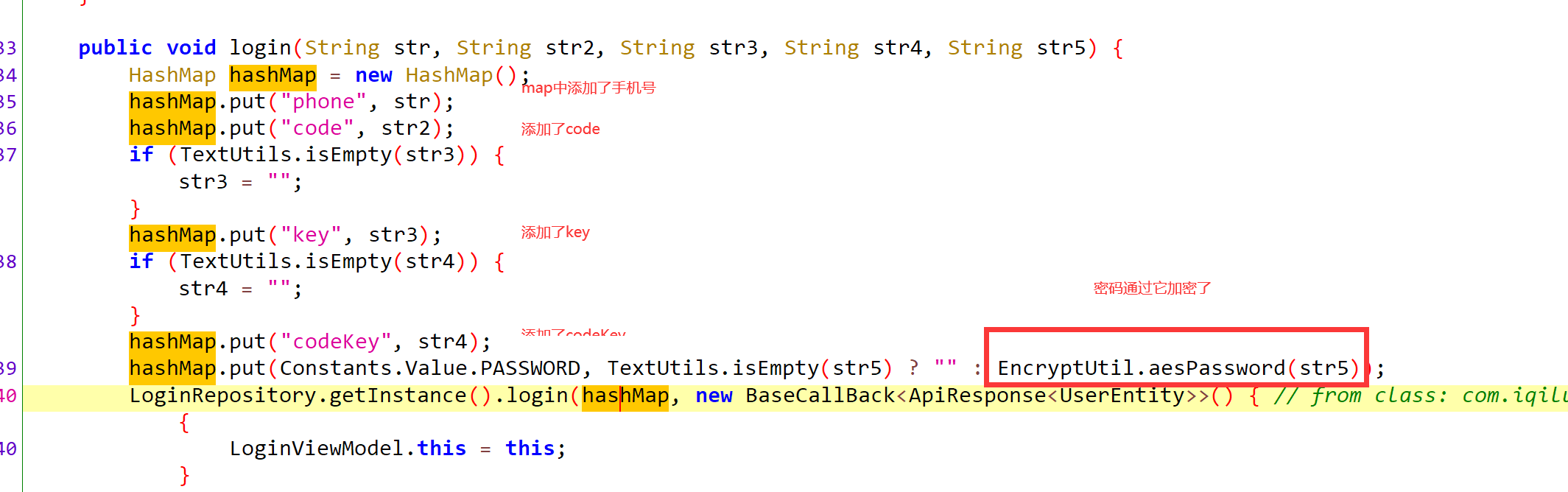
public void login(String str, String str2, String str3, String str4, String str5) {
HashMap hashMap = new HashMap();
hashMap.put("phone", str); # map中添加手机号
hashMap.put("code", str2);# map中添加code,空的
if (TextUtils.isEmpty(str3)) {
str3 = "";
}
hashMap.put("key", str3); # key是空的
if (TextUtils.isEmpty(str4)) {
str4 = "";
}
hashMap.put("codeKey", str4); # map添加codekey,抓包是空的
hashMap.put(Constants.Value.PASSWORD, TextUtils.isEmpty(str5) ? "" : EncryptUtil.aesPassword(str5));
LoginRepository.getInstance().login(hashMap, new BaseCallBack<ApiResponse<UserEntity>>()
# 9 逻辑就是,如果密码不为空,就使用EncryptUtil.aesPassword(str5) 对密码加密
# 10 继续查看加密逻辑,跳到aesPassword的声明
public static String aesPassword(String str) {
return Base64.encodeToString(EncryptUtils.encryptAES(str.getBytes(), getMD5(PRIVATE_KEY + getSecret() + BaseApp.orgid).getBytes(), "AES/CBC/PKCS7Padding", "0000000000000000".getBytes()), 2);
}
#11 通过EncryptUtils.encryptAES 加密后,转了base64--》猜测到是aes加密
-aes加密需要确定的:
-明文是什么
-秘钥是什么
-iv
-加密模式
# 12 调用EncryptUtils.encryptAES(str明文密码,用md5加密的东西,加密模式,0000000000000000)
-点到函数内部发现:第一个参数就是明文,第二个参数是秘钥,第三个参数是加密模式,第四个参数是iv
# 13 一般aes加密,秘钥和iv是固定的,咱们可以看出iv是 0000000000000000
-目前秘钥不知道:咱们可以通过hook,查看它的返回值,返回值直接当秘钥
# 14 通过hook知道了
-明文是什么 lqz12345
-秘钥是什么 6d6656a37cdb7977c10f6d83cab168e9
-iv 0000000000000000
-加密模式 AES/CBC/PKCS7Padding
# 15 python复现密码加密
|